Access Management Policy Template
This policy defines the rules necessary to achieve this.
Access management policy template. Identity and access management policy page 4 responsibilities as well as modification removal or inactivation of accounts when access is no longer required. It is the managers responsibility to ensure that all users with access to sensitive data attend proper training as well as read and acknowledge the university confidentiality agreement. Applying the policy employee access. Users are students employees consultants contractors agents and authorized users.
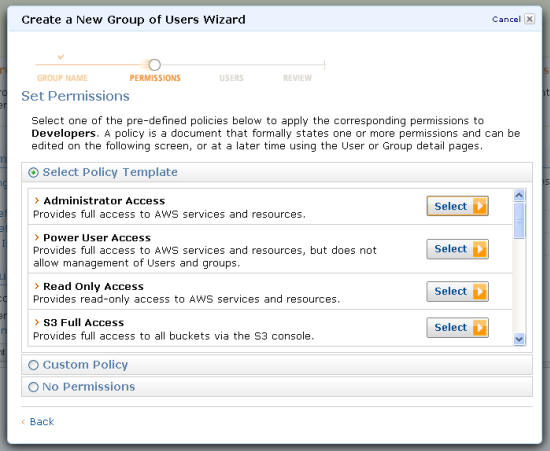
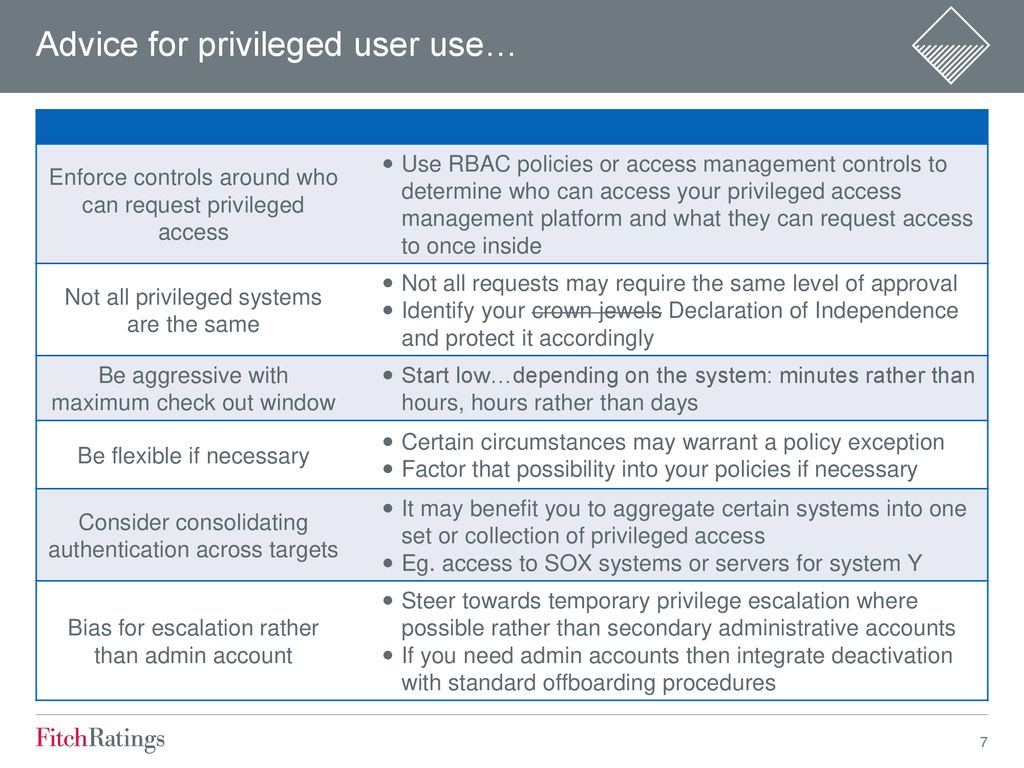
One of the first steps to privileged access management pam success is defining clear and consistent policies that everyone who uses and manages privileged accounts understands and accepts. User access management policies exemplaruser access management policies v11rtf date uncontrolled copy when printed page 6 of 8 unless otherwise advised it operations will delete network access for all leavers at 4pm each friday or on the leaving date if not a friday old user ids are removed and not re issued. You can use this sample policy as a starting point to build a pam policy for your organization. Access control is the process that limits and controls access to resources of a computer system.
Access management policy v31 page 5 of 58 1 introduction this policy is the third version of the access management policy. Management is to immediately notify the security. Nearly all applications that deal with financial privacy safety or defense include some form of access authorization control. Purpose the purpose of this policy is to maintain an adequate level of security to protect company name data and information systems from unauthorized access.
Adequate security of information and information systems is a fundamental management responsibility. Use the template to create your own identity and access management policy to ensure the appropriate use and security of users credentials and that the systems they affect are covered. It access control and user access management policy page 2 of 6 5. Information systems access policy i.
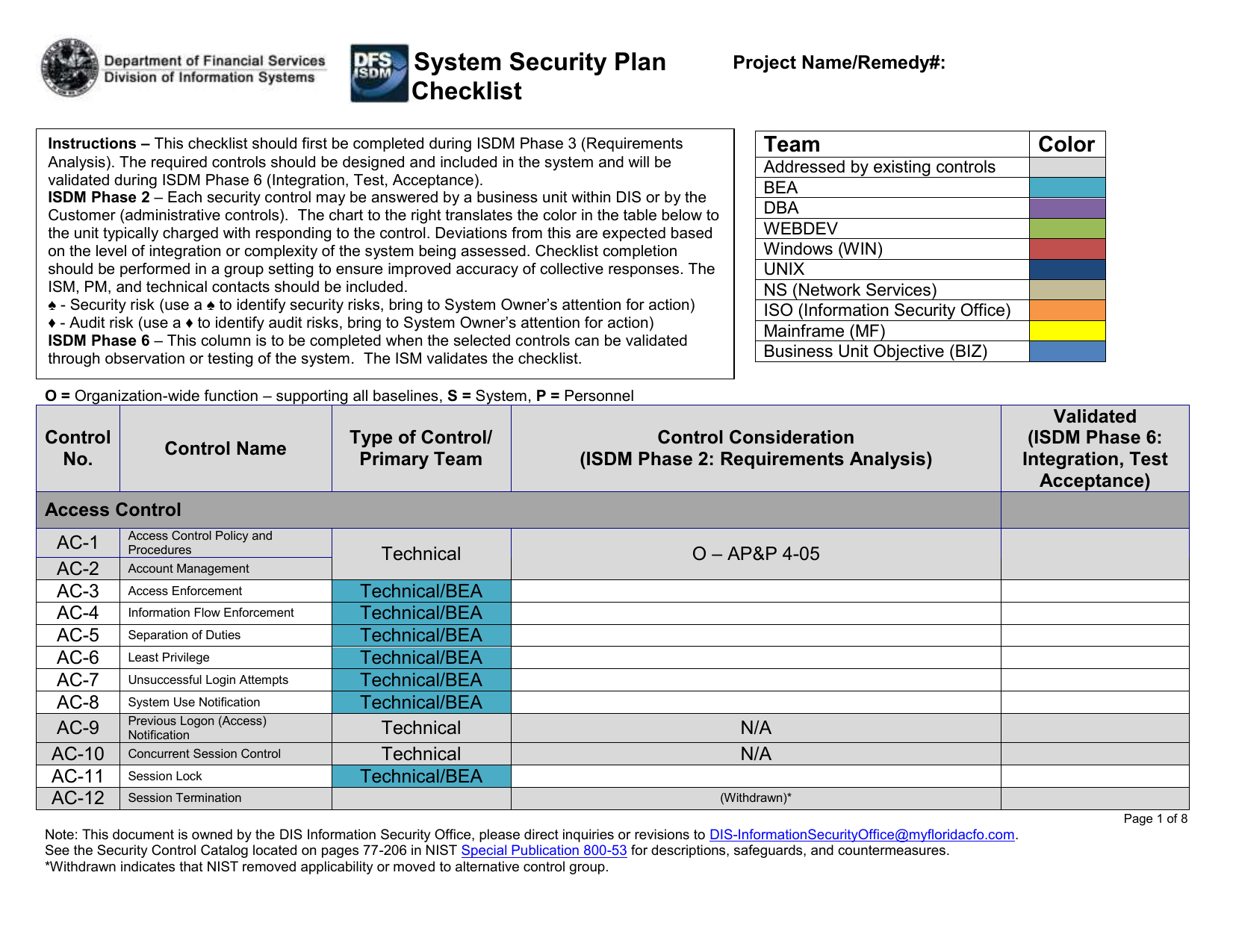
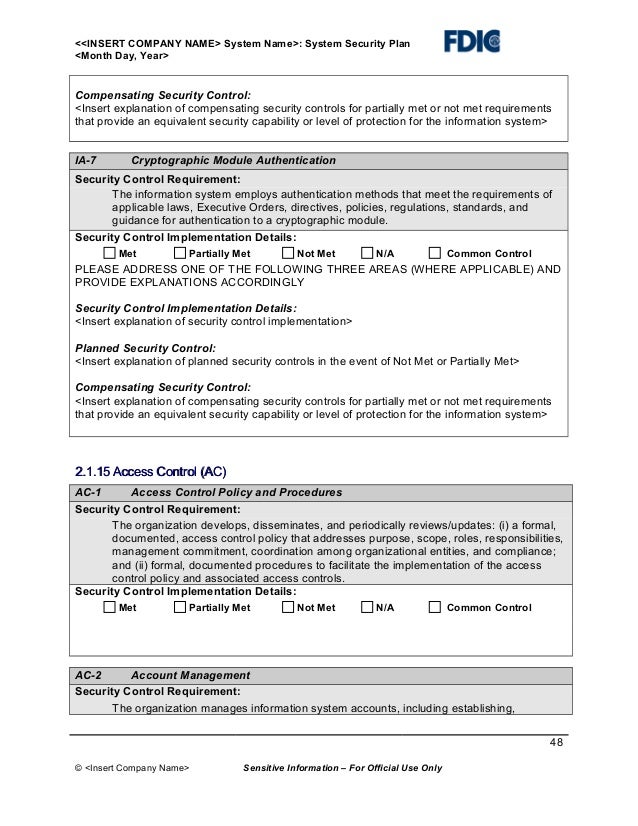
Formal user access control procedures must be documented implemented and kept up to date for each application and information system to ensure authorised user access and to prevent unauthorised access. Kdot authentication resource tracking kart the kdot standard drawings bridge design manuals design software and other forms can now be downloaded with no fee. Identity and access management technology can be used to ensure that services are managed authorized and audited properly within an organization.