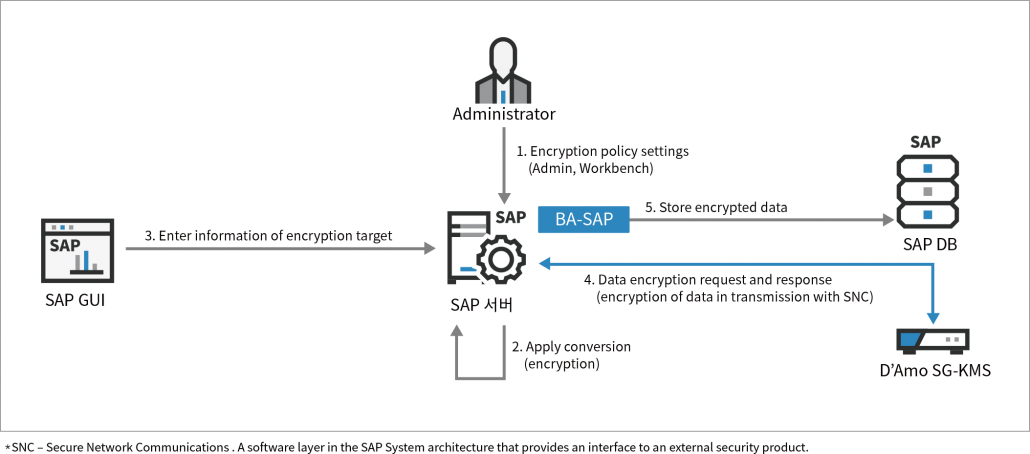
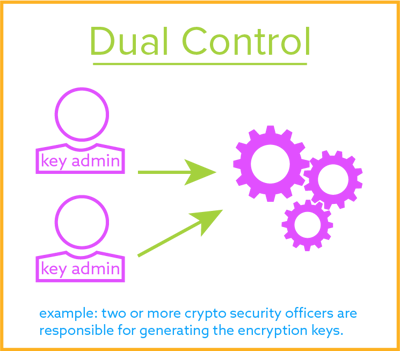
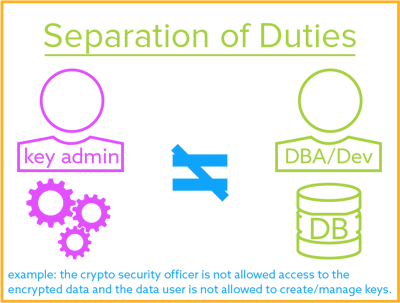
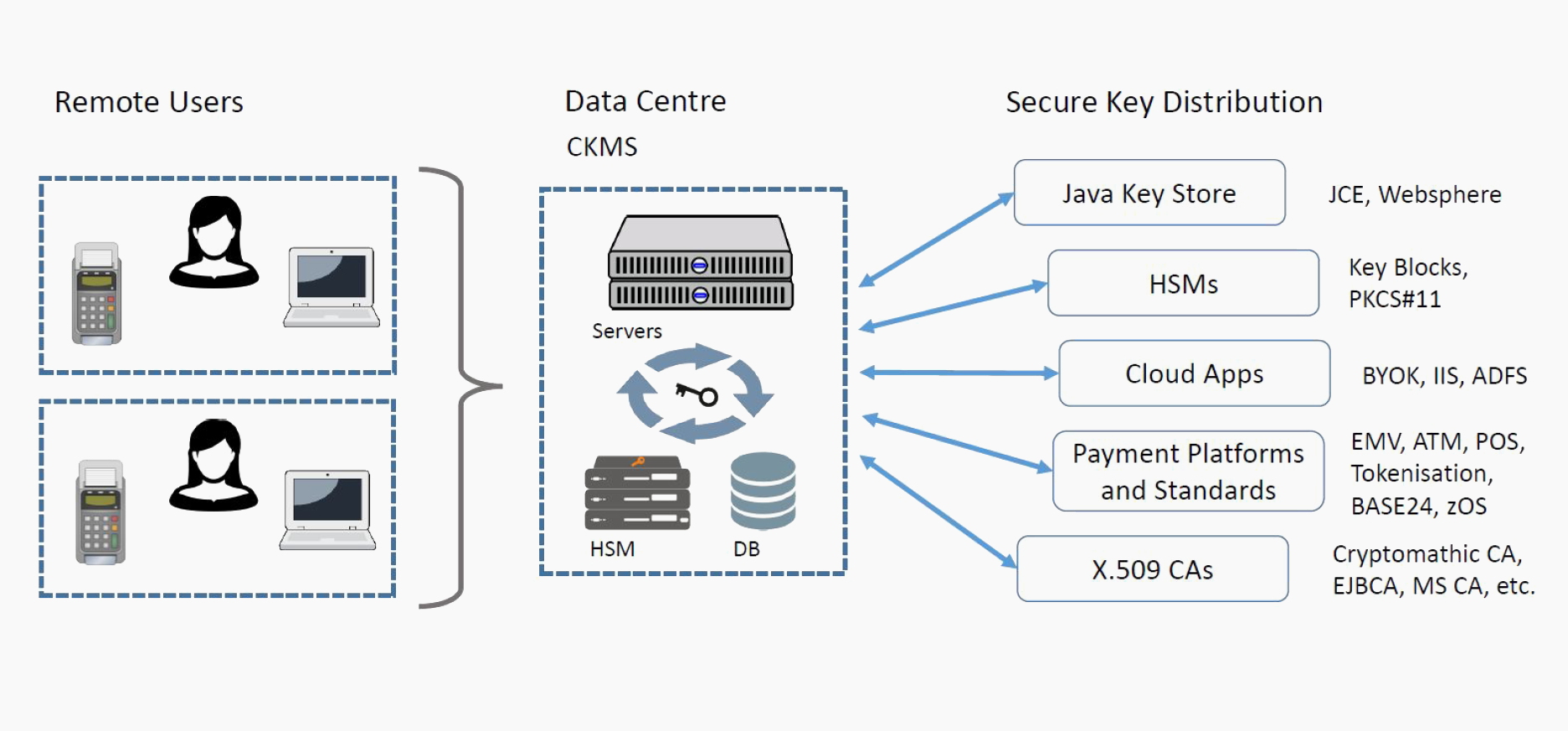
Cryptographic Key Management Policy Template
The cheat sheet series project has been moved to github.
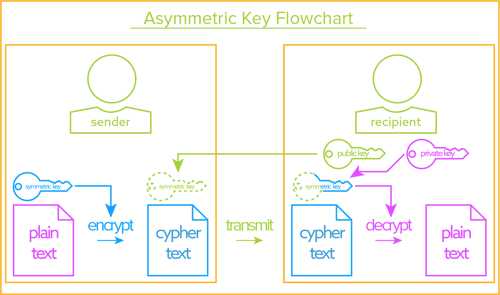
Cryptographic key management policy template. In this article we share the ict institute data encryption policy that is. Encryption methods and key management procedures. A key management policy kmp is a high level set of rules that are established by an organization to describe the goals responsibilities and overall requirements for the management of cryptographic keying material used to protect private or critical facilities processes or information. Public key cryptography public key pairs.
Learn how the annex a10 of iso 27001 can help you define a policy on the use of cryptographic controls certificates and other confidential information. Government laws documents and regulations relevant to the employment of cryptography and provides a sample structure and content for organizational key management policies kmp and key management practices statements kmps. How to use the cryptography according to iso 27001 control a10. To make sure it is used in the right way it is recommended by standards such as iso 27002 have a data encryption policy.
Diffie hellman ike or elliptic curve diffie hellman ecdh. 43 key agreement and authentication 431 key exchanges must use one of the following cryptographic protocols. When the key for encrypting and. In general company name adheres to the nist policy on hash functions.
September 25 2015. These statements include authorization and protection objectives. Division of information technology policy 101a use of cryptographic controls policy initially approved. On the other hand to encrypt the information a key is generally needed.
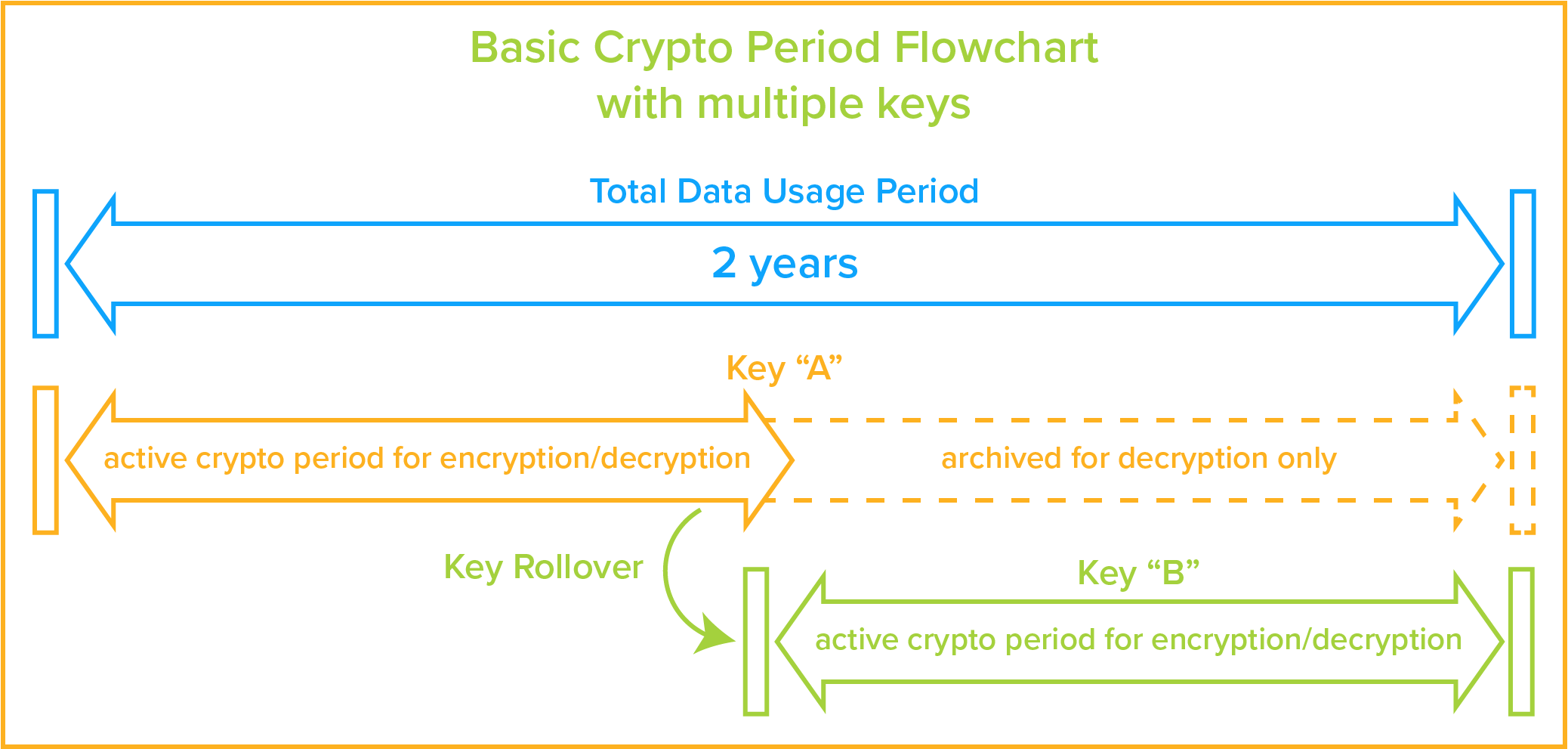
Infosec personnel will direct the end user in. Using cryptographic controls such as encryption can help with information security but only if it is applied correctly. A acceptable cryptographic key lengths and b acceptable cryptographic algorithms. Encryption key management if not done properly can lead to compromise and disclosure of.
The hardest part of implementing strong encryption is securely and effectively managing keys and policies. The loss theft or potential unauthorized disclosure of any encryption key covered by this policy must be reported immediately to the infosec team. Without strong and flexible systems in place to do that the best encryption standards are useless. Scope and application of the policy cryptographic controls can be used to achieve different information security objectives eg.
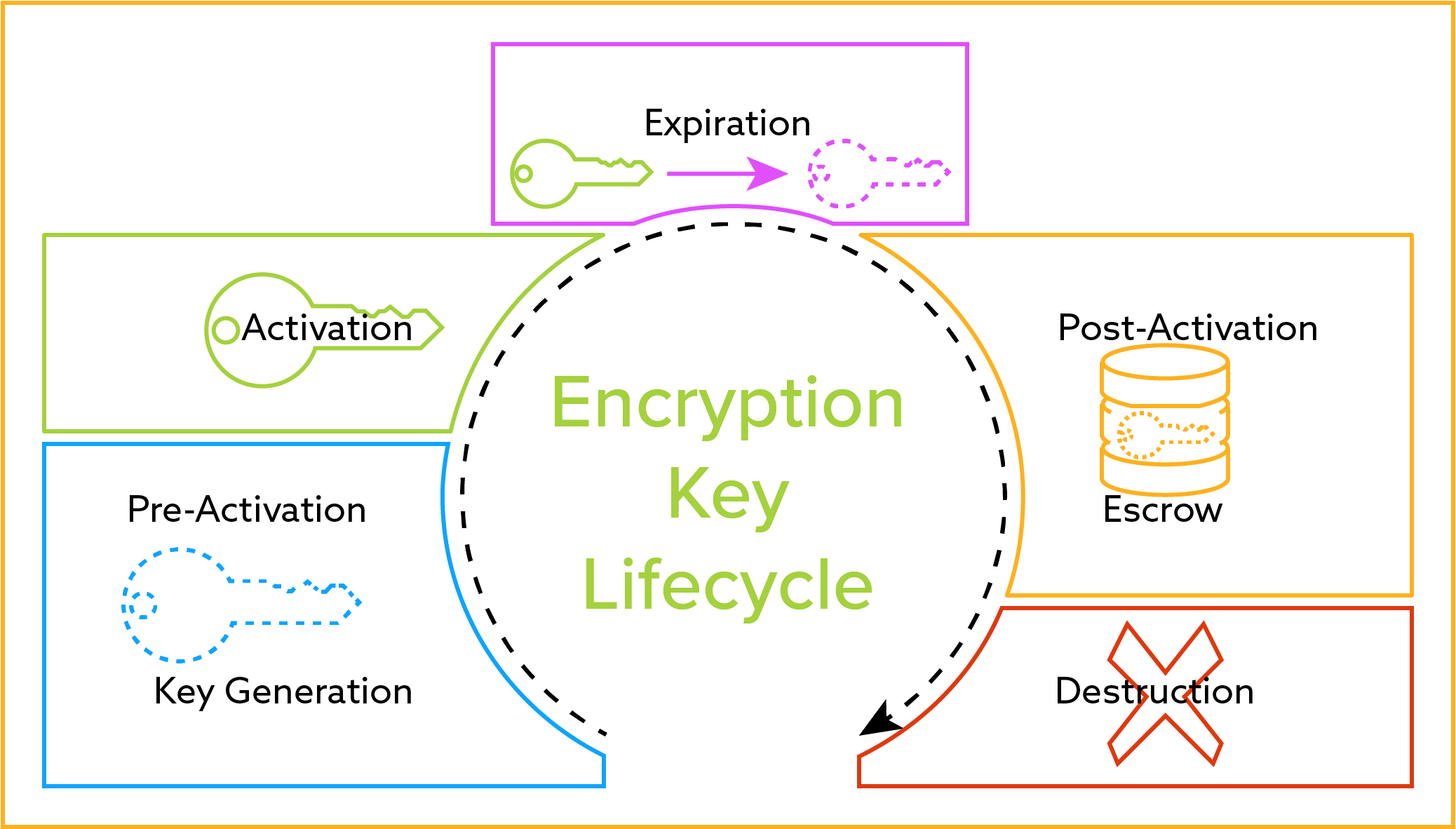
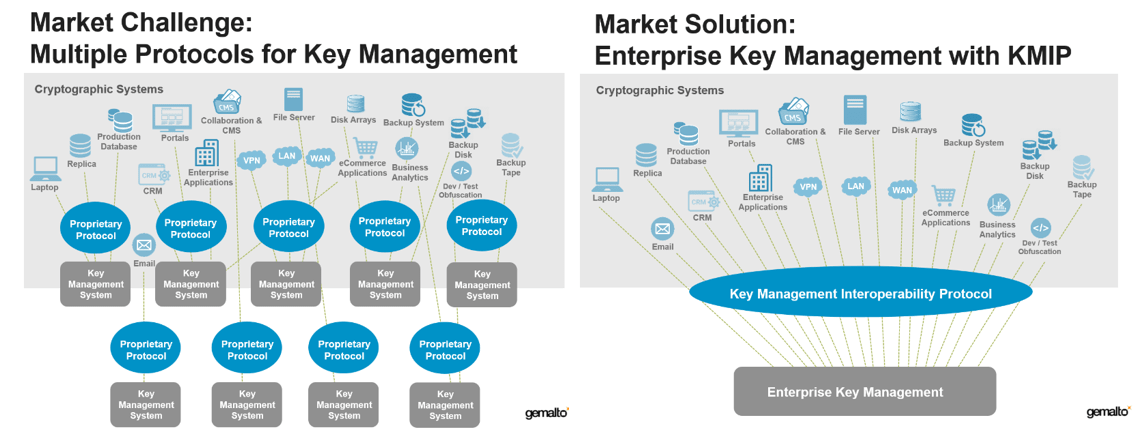
7 essential elements to effective key management policy. Larger key spaces however are recommended for longer term security. Please visit key management cheat sheet to see the latest version of the cheat sheet. The key management policy and practices subsection identifies us.