Fips Certification Process
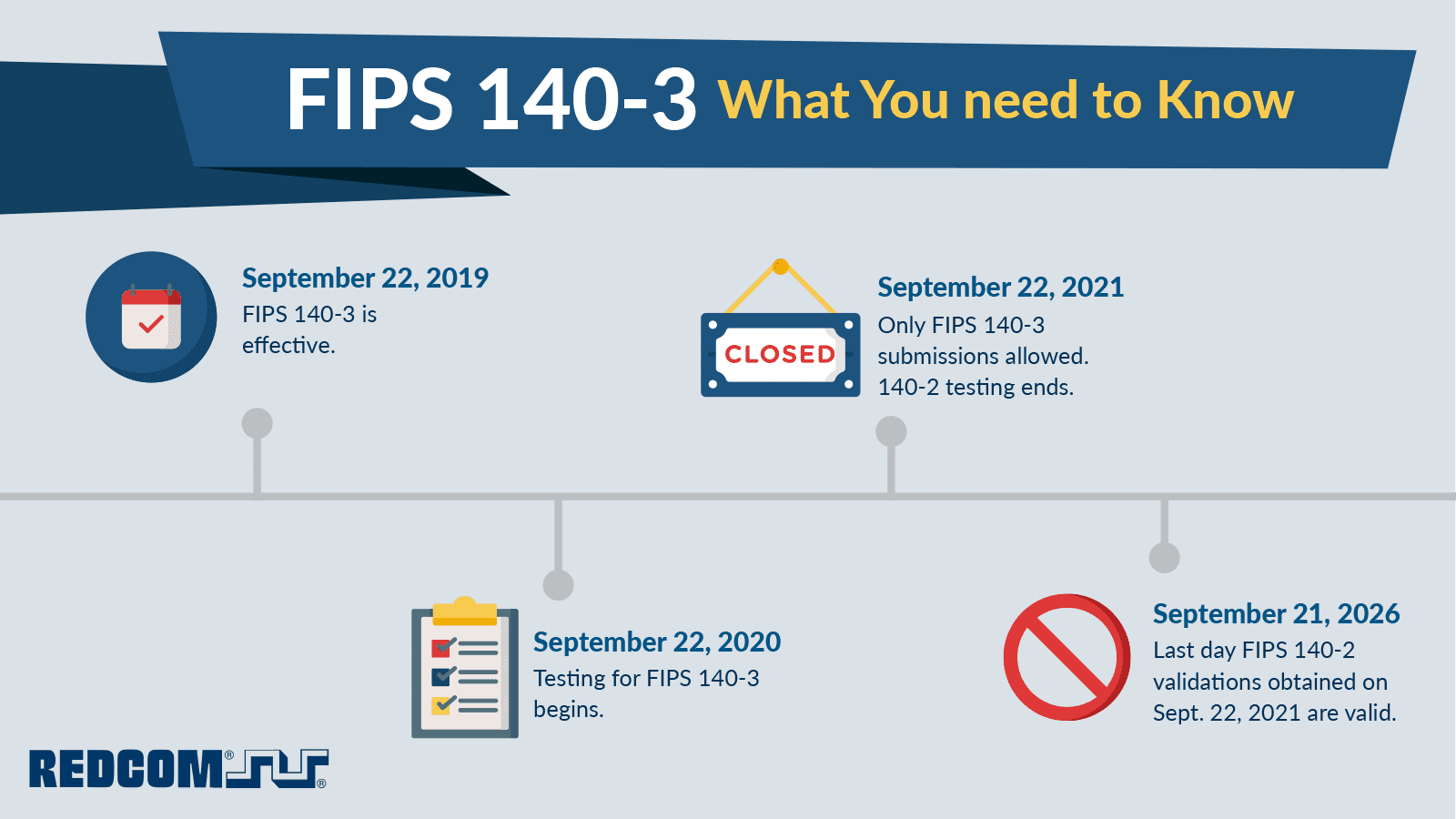
The title is security requirements for cryptographic modulesinitial publication was on may 25 2001 and was last updated december 3 2002.
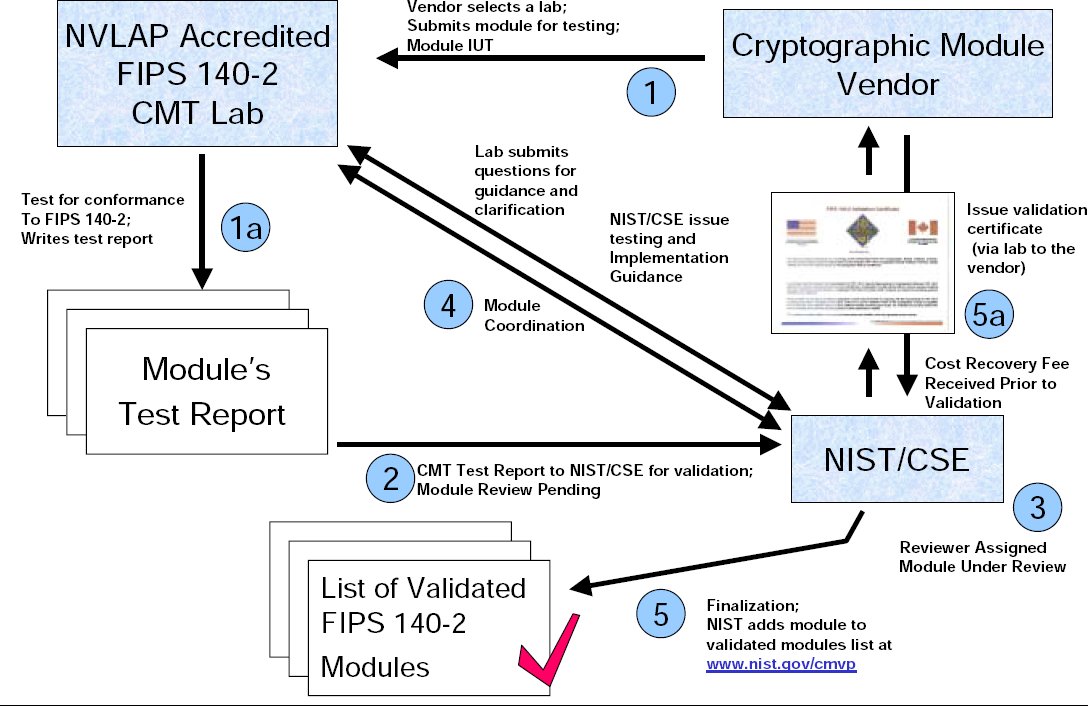
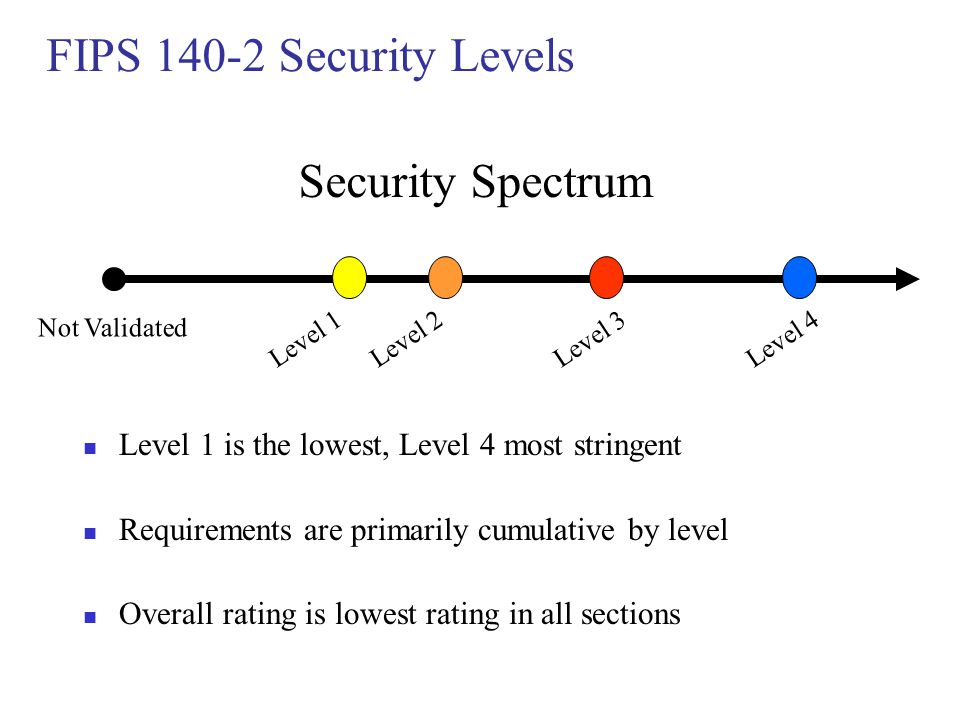
Fips certification process. Modules in process list the mip list contains cryptographic modules on which the cmvp is actively working. For example level 3 ensures that the code is within a tamper proof container so thatkeys used in. The cryptographic module validation program cmvp fips 140 2 modules in process and implementation under test iut lists are provided for information purposes onlyparticipation on the list is voluntary and is a joint decision by the vendor and cryptographic security and testing cst laboratory. Level 1 examines the algorithms used in the cryptographic component of the software.
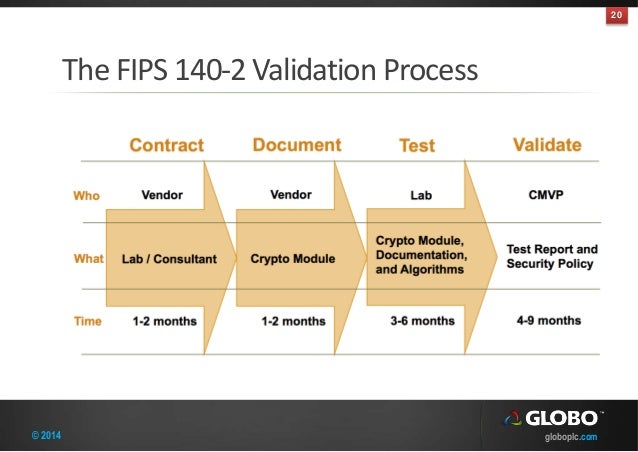
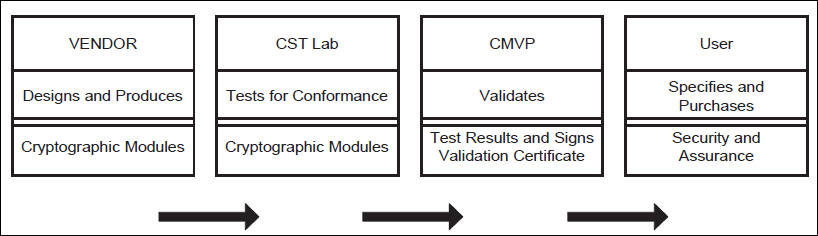
On july 17 1995 nist established the cryptographic module validation program cmvp that validates cryptographic modules to federal information processing standards fips140 1 security requirements for cryptographic modules and other fips cryptography based standards. The fips 140 2 validation process examines the cryptographic modules. At each stage. Use this form to search for information on validated cryptographic modules.
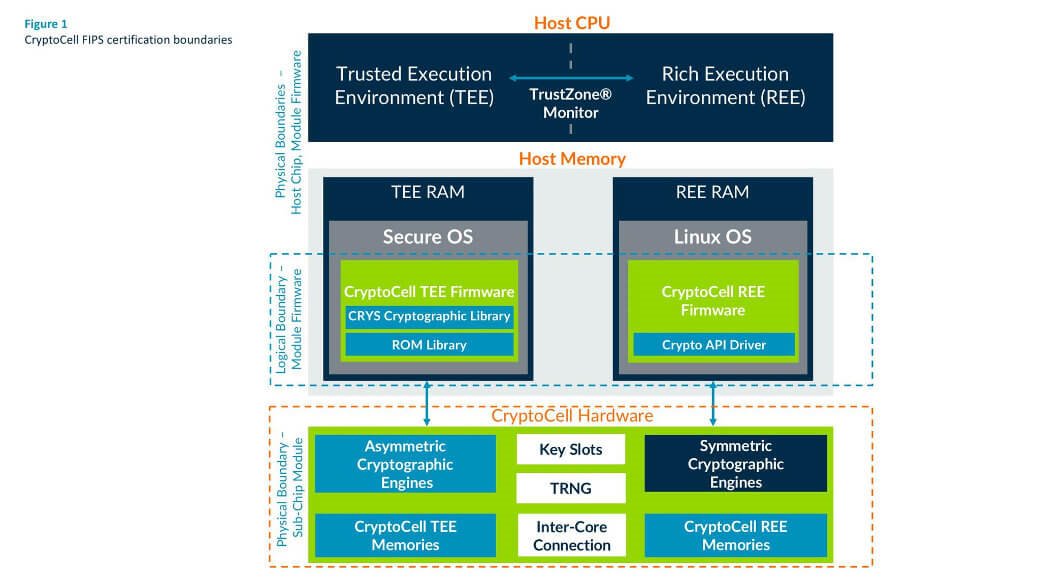
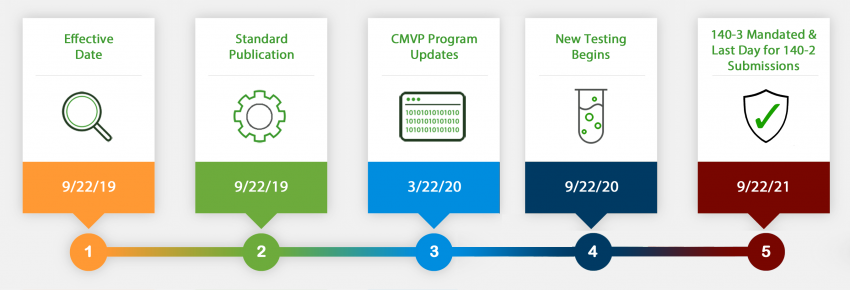
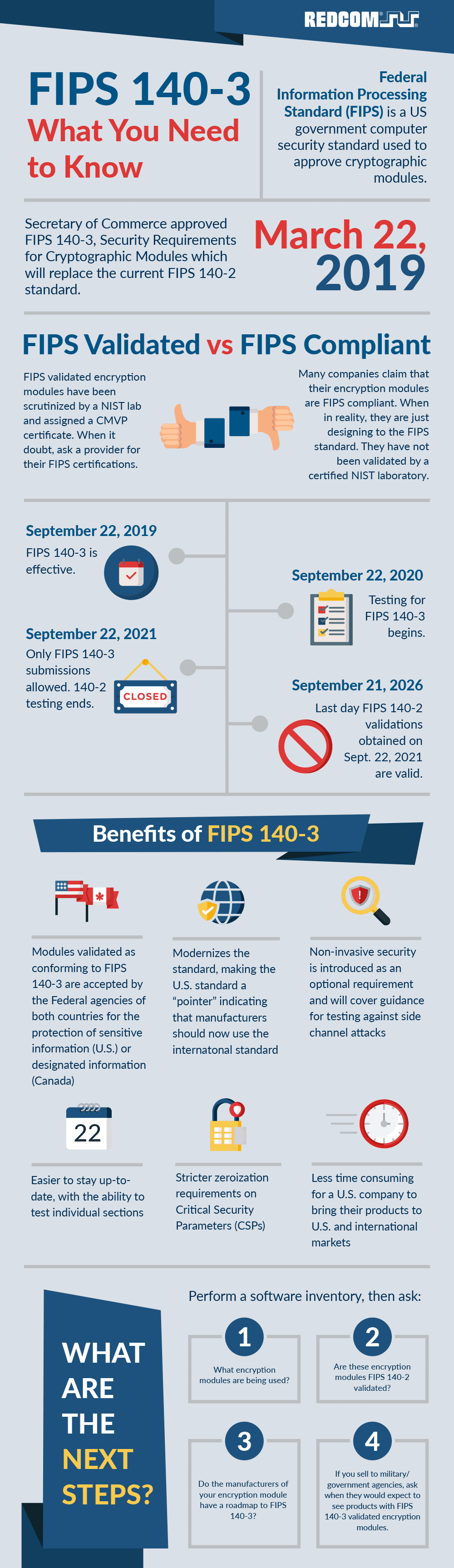
Security requirements are outlined in full within the nist fips 140 2 pub. Government computer security standard used to approve cryptographic modules. The federal information processing standard publication 140 2 fips pub 140 2 is a us. There are five major stages that need to be addressed in order to complete a fips 140 2 validation.
Do you look at source code. How long does it take. Federal agencies are required to complete fips 140 2 validation if they use cryptography in security systems that process sensitive but unclassified sbu information. The fips certification process requires that you use algorithms that are approved by the national institute for standards and technology and the communications security establishment canada and are listed in annex a of the fips 140 2 standard.
For a module to transition from review pending to in review the lab must first pay the nist cost recovery fee and then the report will be assigned as resources become available. What is the process to complete fips 140 2 validation. Select the basic search type to search modules on the active validation list. Levels 2 4 build on the software component by adding different layers of physical security.
Fips 140 2 security requirements for cryptographic modules was released on may 25 2001. The fips 140 1 and fips 140 2 validated modules search provides access to the official validation information of all cryptographic modules that have been tested and validated under the cryptographic module validation program as meeting requirements for fips pub 140 1 and fips pub 140 2. Certification strategy product security hardening documentation laboratory and algorithm testing and government review.