Network Security Report Template
Governance risk management and compliance is a substantial part of any information assurance program.
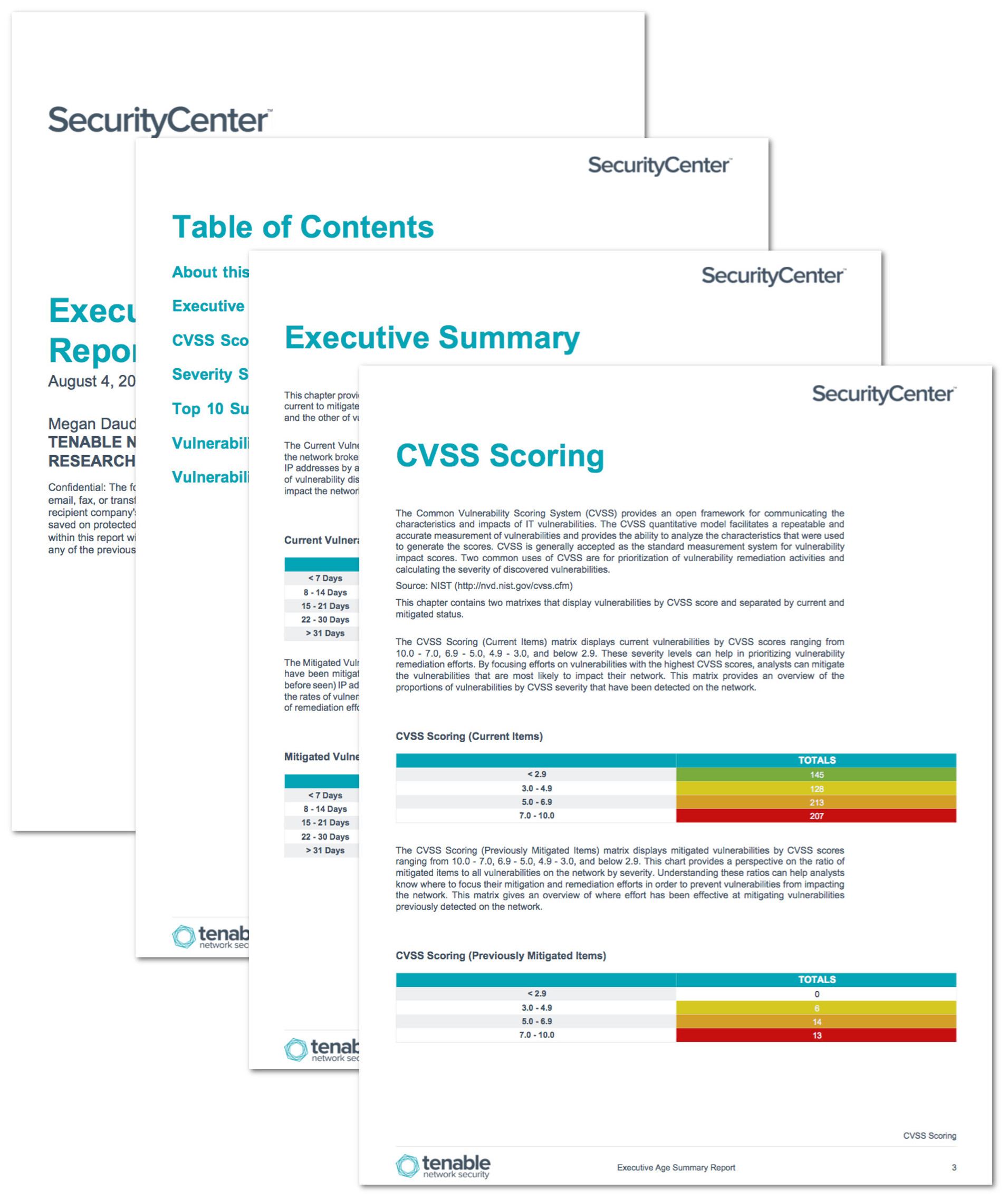
Network security report template. Nessus professional will help automate the vulnerability scanning process save time in your compliance cycles and allow you to engage your it team. Businesses can use this it incident report template to report incidents such as data breaches privacy violations viruses and denial of service attacks. Analyze the data collected during the assessment to identify relevant issues. A network assessment template enables assessment of security threats identifying possible causes and mitigating risks.
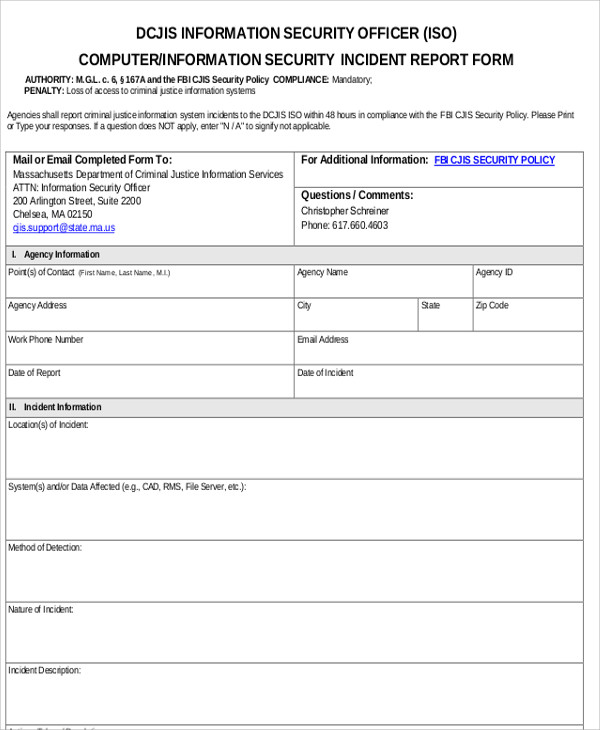
Nist sp 80039 managing information security risk risk analysis scope the scope of this risk assessment encompasses the potential risks and vulnerabilities to the confidentiality availability and integrity of all systems and data that acme creates receives maintains or transmits. Prioritize your risks and observations. The grc requires information systems to be audited regardless of the standard to which the audit is performed. You may also see incident report forms.
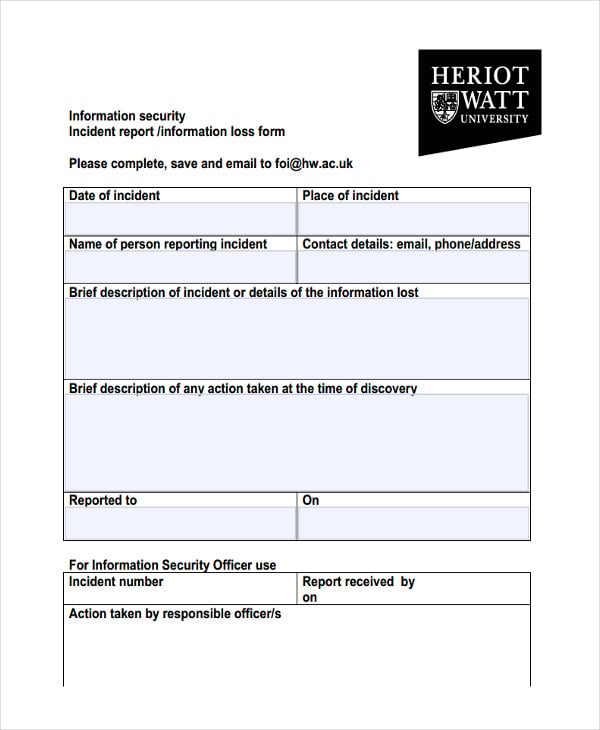
Templates should at a minimum cover. The security 2 command class specifications outlined in the document security 2 command class version 1 alpha s0 s2 security command class document number. They provide comprehensive safety measures to protect and use network systems with great care by drafting various policies. Who the person or persons involved in the incident.
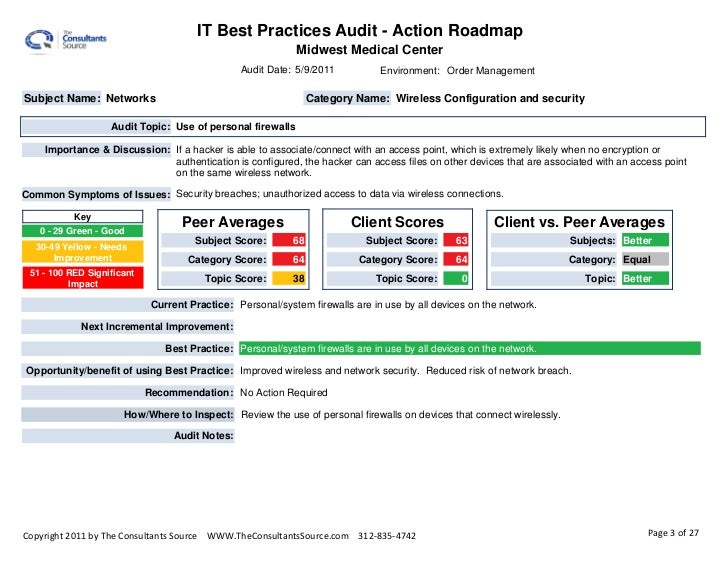
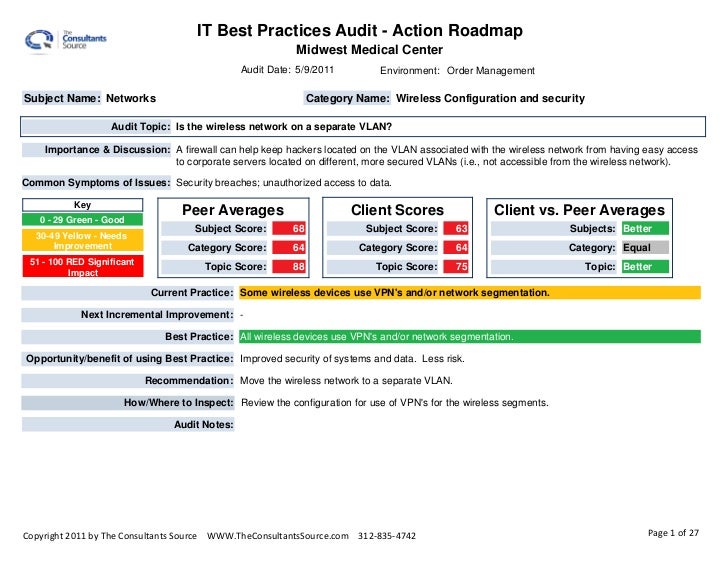
High level design as a summary how this part of the network connects to the broader network. Describe your prioritized findings and recommendations. A security incident report should follow the five basics of reporting. Network device audit reports.
General approach to creating the report. How to write an executive report writing a security report for executives doesnt have to be difficult or extensive but security management expert ernie hayden describes. Nessus is the most comprehensive vulnerability scanner on the market today. It was not possible to recover the network key during the course of the assessment.
Document the assessment methodology and scope. What details of the incident and summary of report. Templates describe how a site or data center or part of the data center should be configured. Templates form the basis for network design and engineering particularly for offices and data centers.