Ransomware Policy Template

So in that spirit weve decided to bust our cyber awareness email templates out of the vault and post them here for you to use in your organization.
Ransomware policy template. This document goes into the details of multiple stages of a ransomware attack and describes a multilayer offensive security approach to protect an organization from ransomware attacks. As more federal agencies release alerts on ransomware organizations should update healthcare data security policies to include. So you may need a ransomware policy. Learn how to protect yourself and how to report suspicious communications containing ransomware.
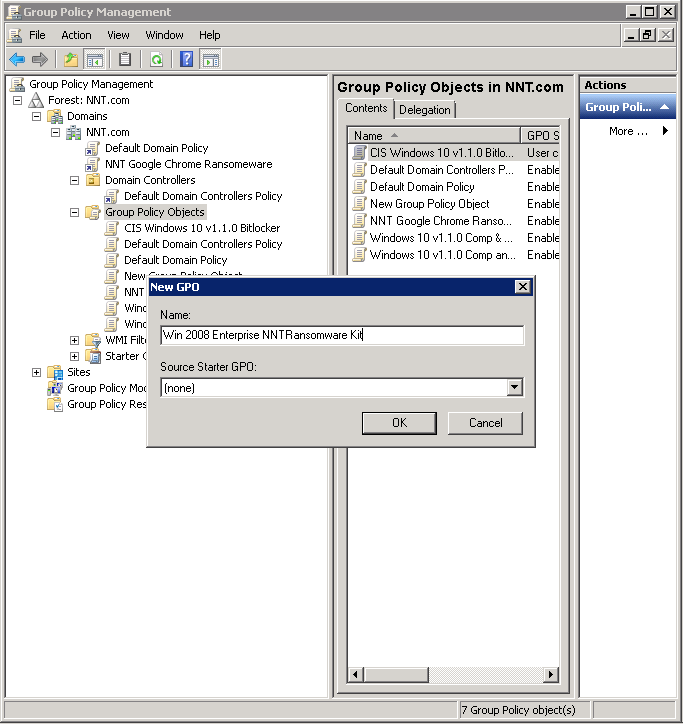
Its listed as ransomware policy with a little new sign after it. After the initial infection the ransomware attempts to spread to shared storage drives and other accessible systems. Below you can find email templates for the four most common cyber awareness topics. The sample security policies templates and tools provided here were contributed by the security community.
Ransomware phishing whaling and password tips. If the demands are not met the. Detect potential ransomware on your cloud environment by creating a policy to update you when suspicious activity is detected and set up automated actions to prevent ransomware files from being saved to your cloud. Remote access email and supply chain primarily intended for an executive audience the paper should be helpful to.
Connect at least one cloud app office 365 g suite box and dropbox to cloud app security. Ransomware is a type of malicious software designed to block access to a computer system or data until a ransom is paid. Ransomware prevention and response for cisos document provides and aggregate of already existing federal government and private industry best practices and mitigation strategies focused on the. The scope and sophistication of ransomware is evolving at very high rate and there is a need to develop a cyber security model against ransomware attacks.
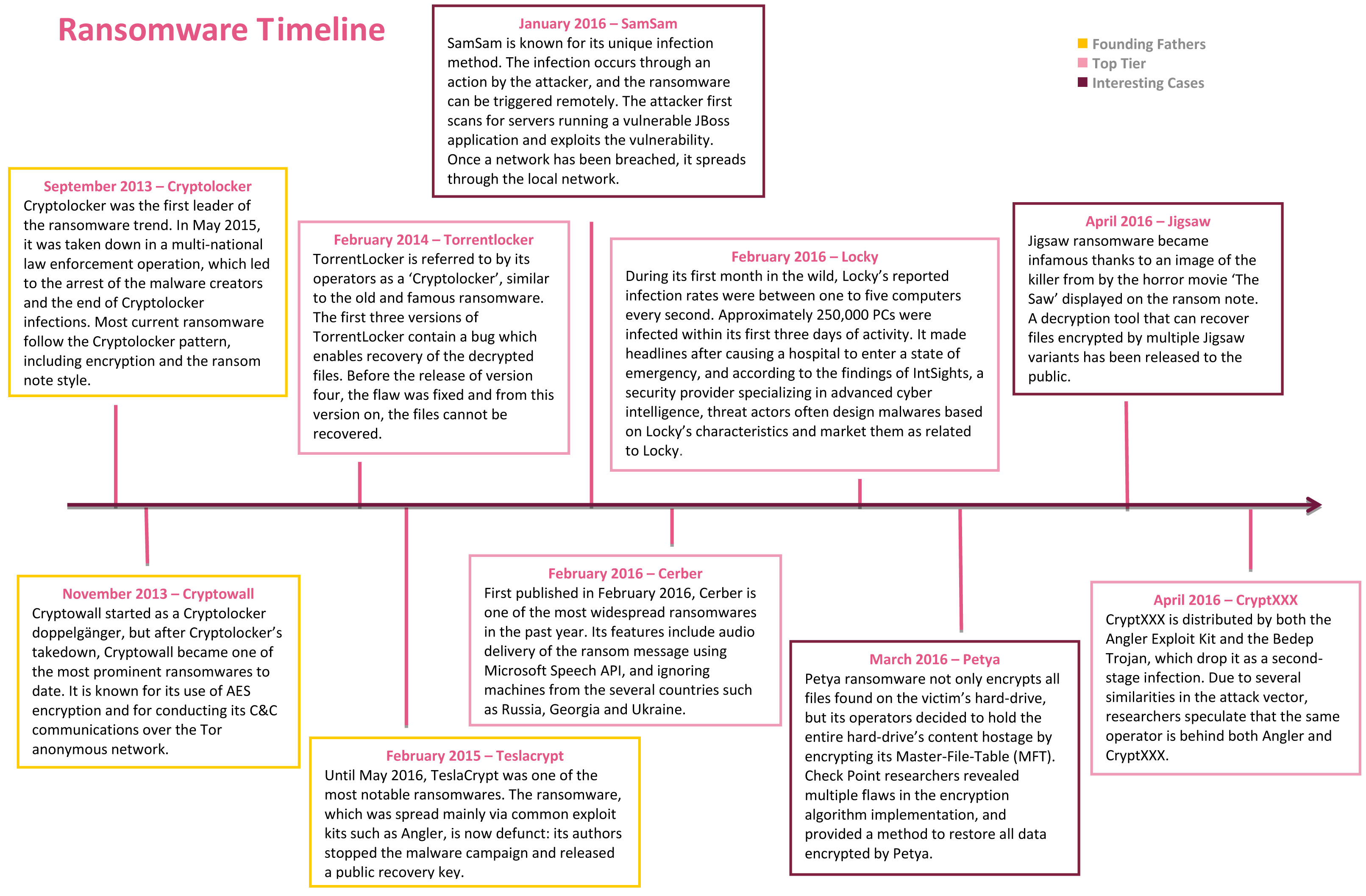
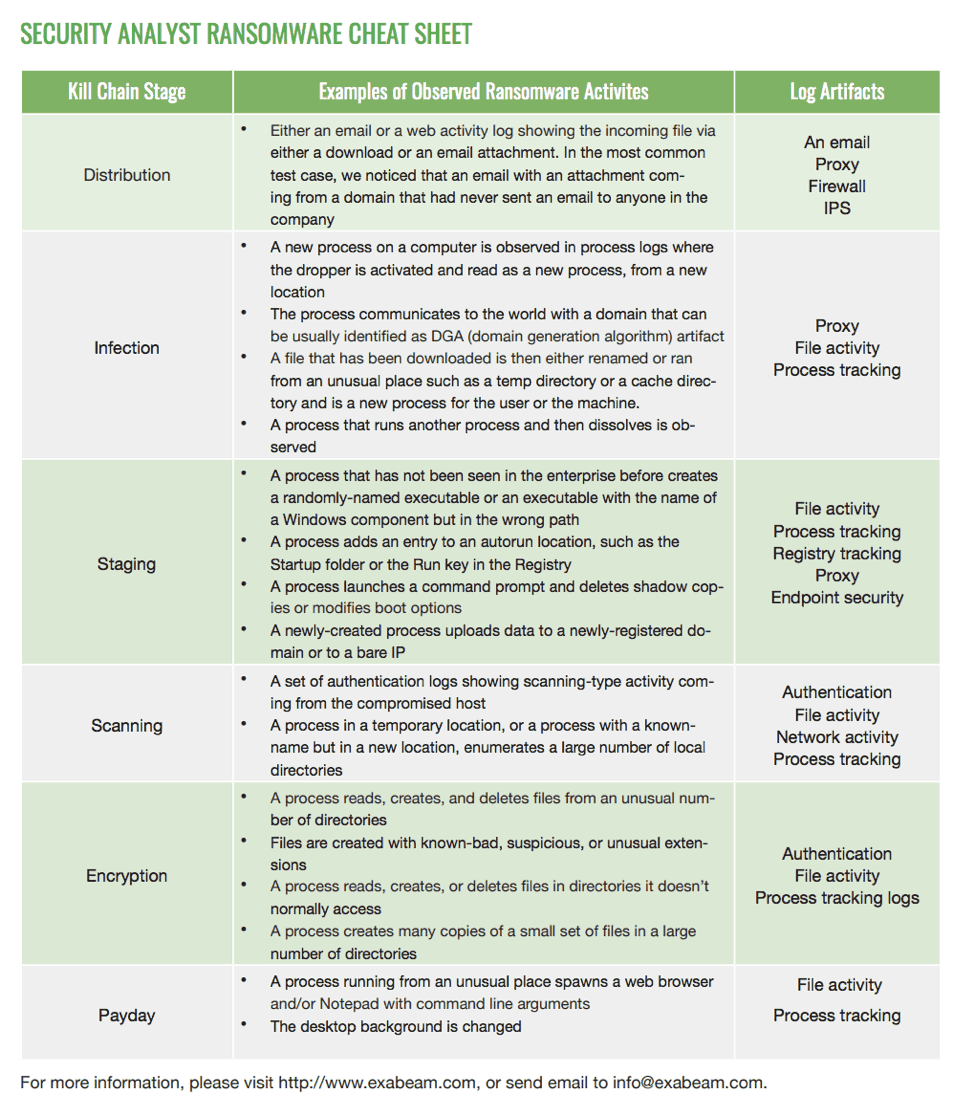
The malicious cyber actor holds systems or data hostage until the ransom is paid. Ransomware attacks three ransomware attack vectors are addressed in this order. Ransomware is a type of malicious software cyber actors use to deny access to systems or data.