Cyber Security Incident Response Playbook Template

Customers can significantly save time on manual and repetitive tasks respond to incidents with pinpoint accuracy accelerate mean time to resolution and maintain greater control over it infrastructure.
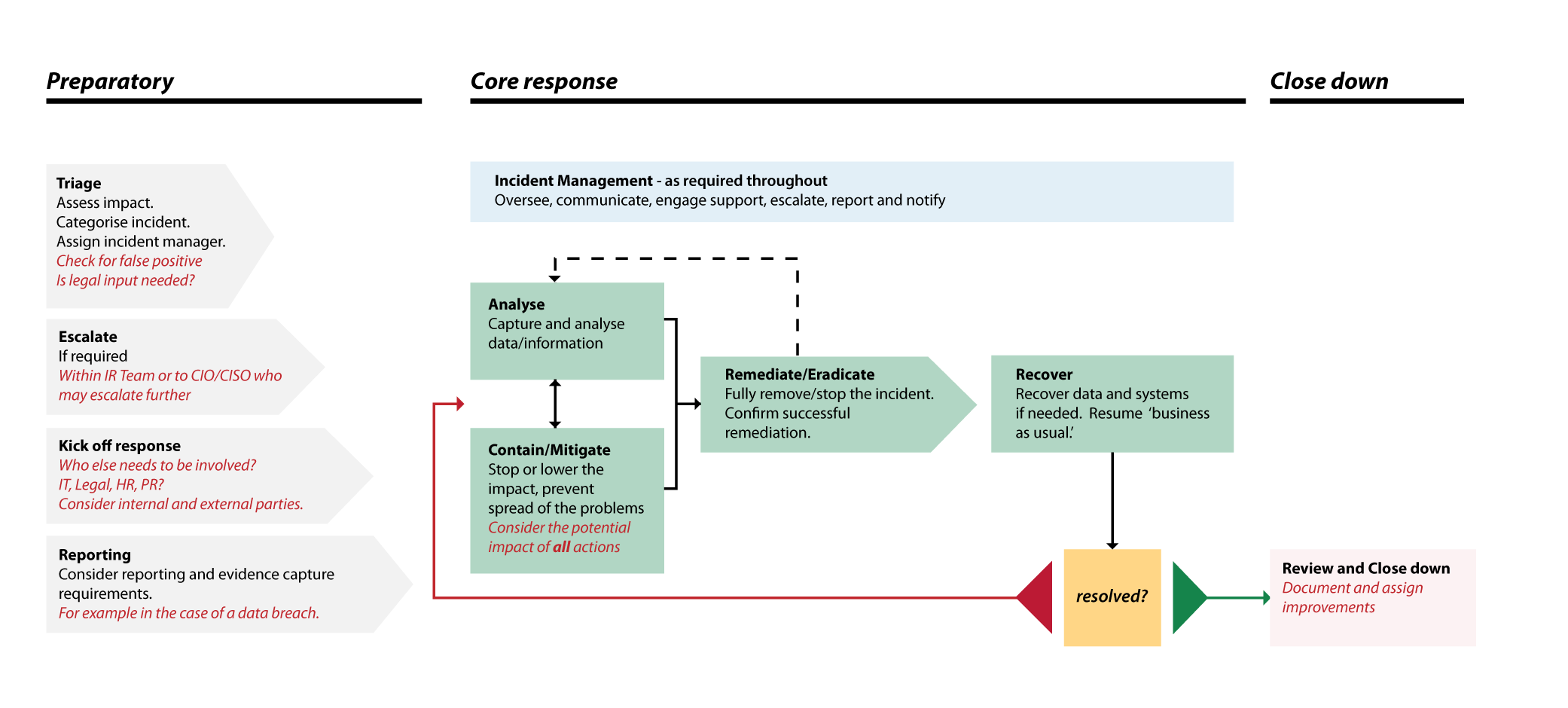
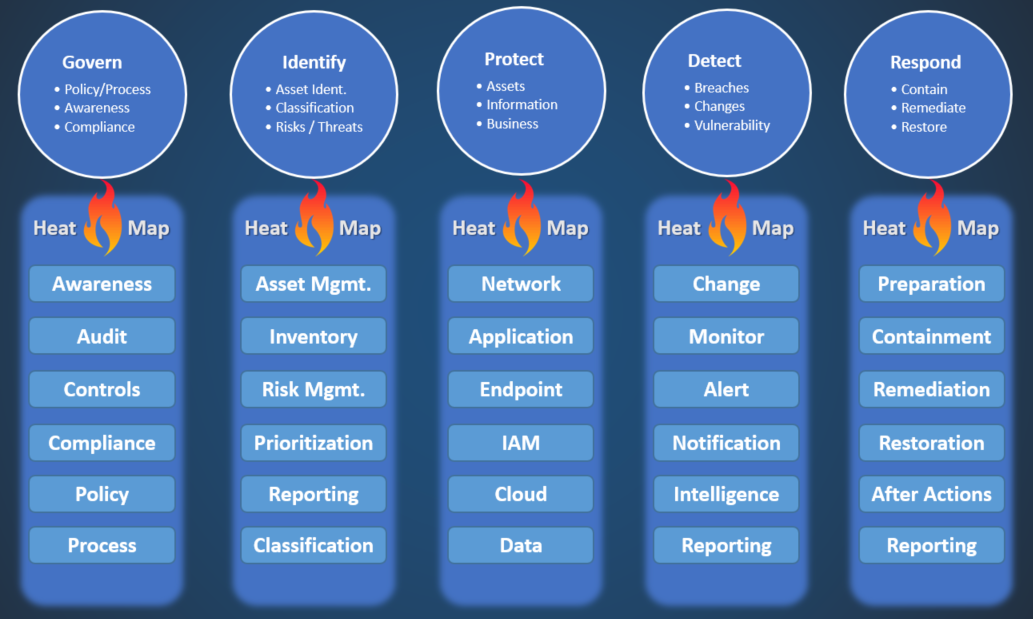
Cyber security incident response playbook template. Training and drills for one organic team soc or incident response in any cyber attack of choice. Because performing incident response effectively is a complex undertaking establishing a successful incident response capability requires substantial planning and resources. The publication supplies tactical and strategic guidance for developing testing and improving recovery plan s and calls for organizations to create a specific playbook for each possible cyber security incident. Ors 182122 requires agencies to develop the capacity to respond to incidents that involve the security of information.
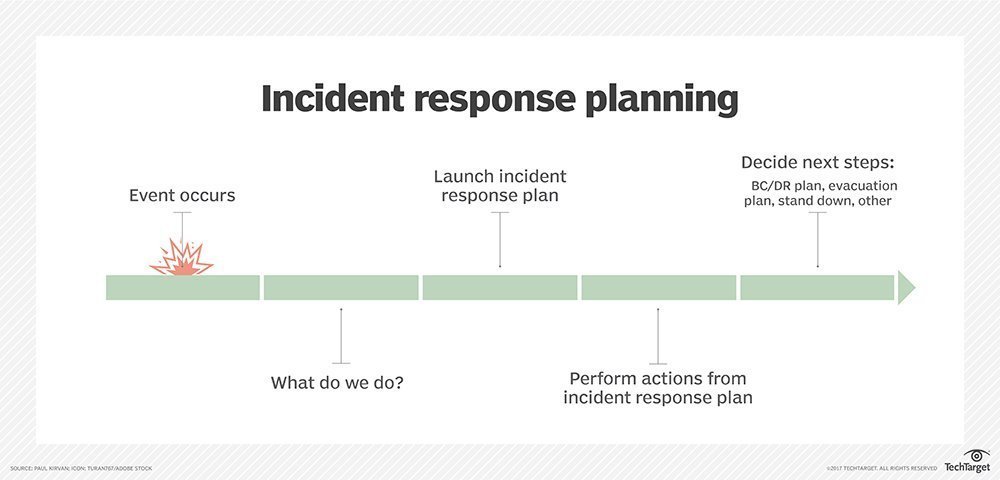
The first event of the playbook process triggers the rest of the steps and is often the security issue addressed by the entire playbook. The first and only incident response community laser focused on incident response security operations and remediation processes concentrating on best practices playbooks runbooks and product connectors. Once the incident response team is defined and aware of their position key action steps of a cyber security incident need to be put in place. Powered by machine learning algorithms it acts as a force multiplier for it operations security operations managed service providers msps and managed security service providers mssps.
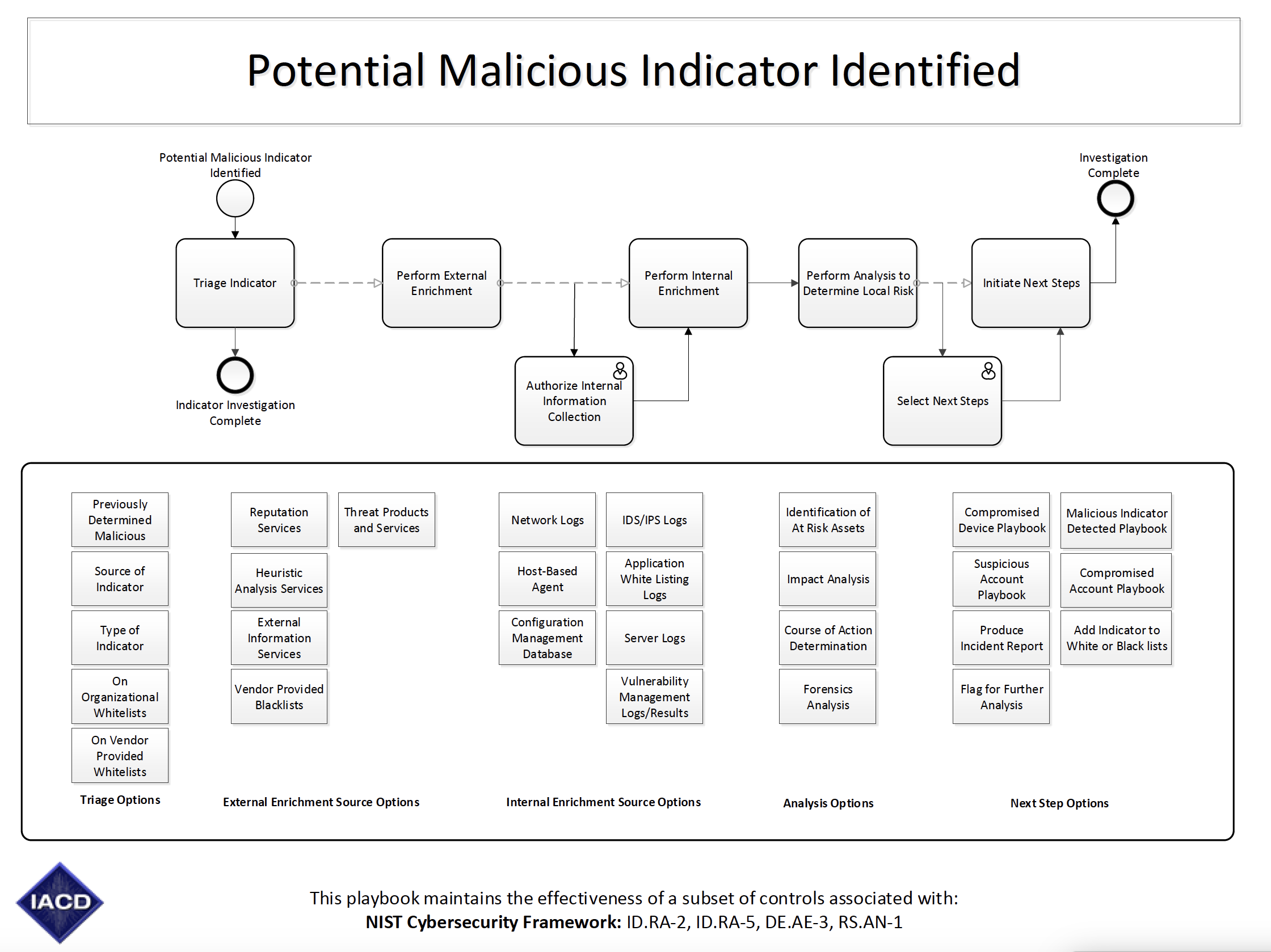
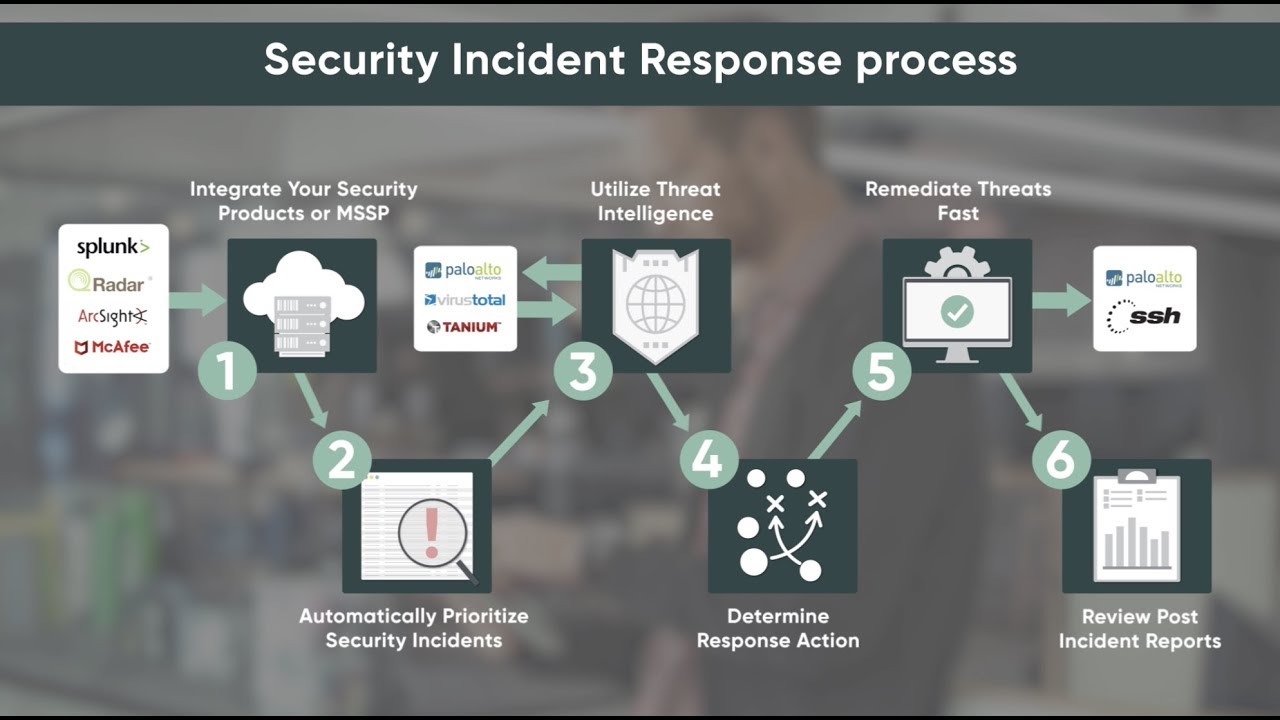
Cyber security the strategy policy and standards regarding the security of and operations in cyberspace. Incident response playbooks can be shared across organizations and include common components such as. The guide provides examples of playbooks to handle data breaches and ransomware. The purpose of a security playbook is to provide all members of an organization with a clear understanding of their responsibilities towards cybersecurity standards and accepted practices before during and after a security incident.
Playbook tabletop exercises give teams an opportunity to do a dry run through incident response playbooks and are a great tool to allow incident response teams to become more acquainted with the different playbooks and their pitfalls. Encompasses the full range of threat reduction vulnerability reduction deterrence international engagement incident response resiliency and recovery policies and activities including computer network operations information. The open source cybersecurity playbook tm phishing what it is. Security incident response plan template was created to align with the statewide information security incident response policy 107 004 xxx.
Agencies must implement forensic techniques and remedies and.