Vulnerability Management Plan Template

Cost savings estimate vulnerability patch management program vpmp when you look at the costs associated with either 1 hiring an external consultant to write cybersecurity documentation for you or 2 tasking your internal staff to write it the cost comparisons paint a clear picture that buying from complianceforge is the logical option.
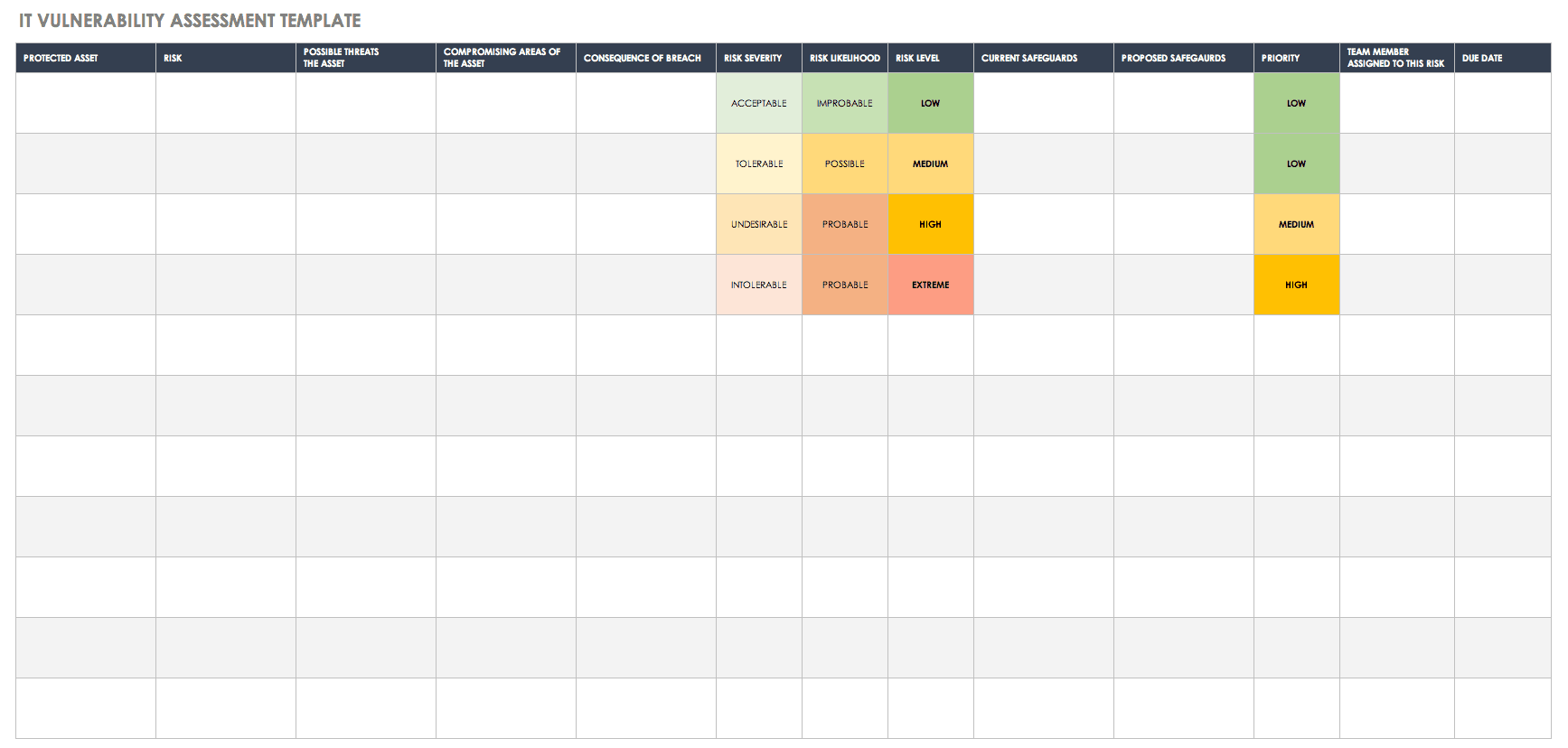
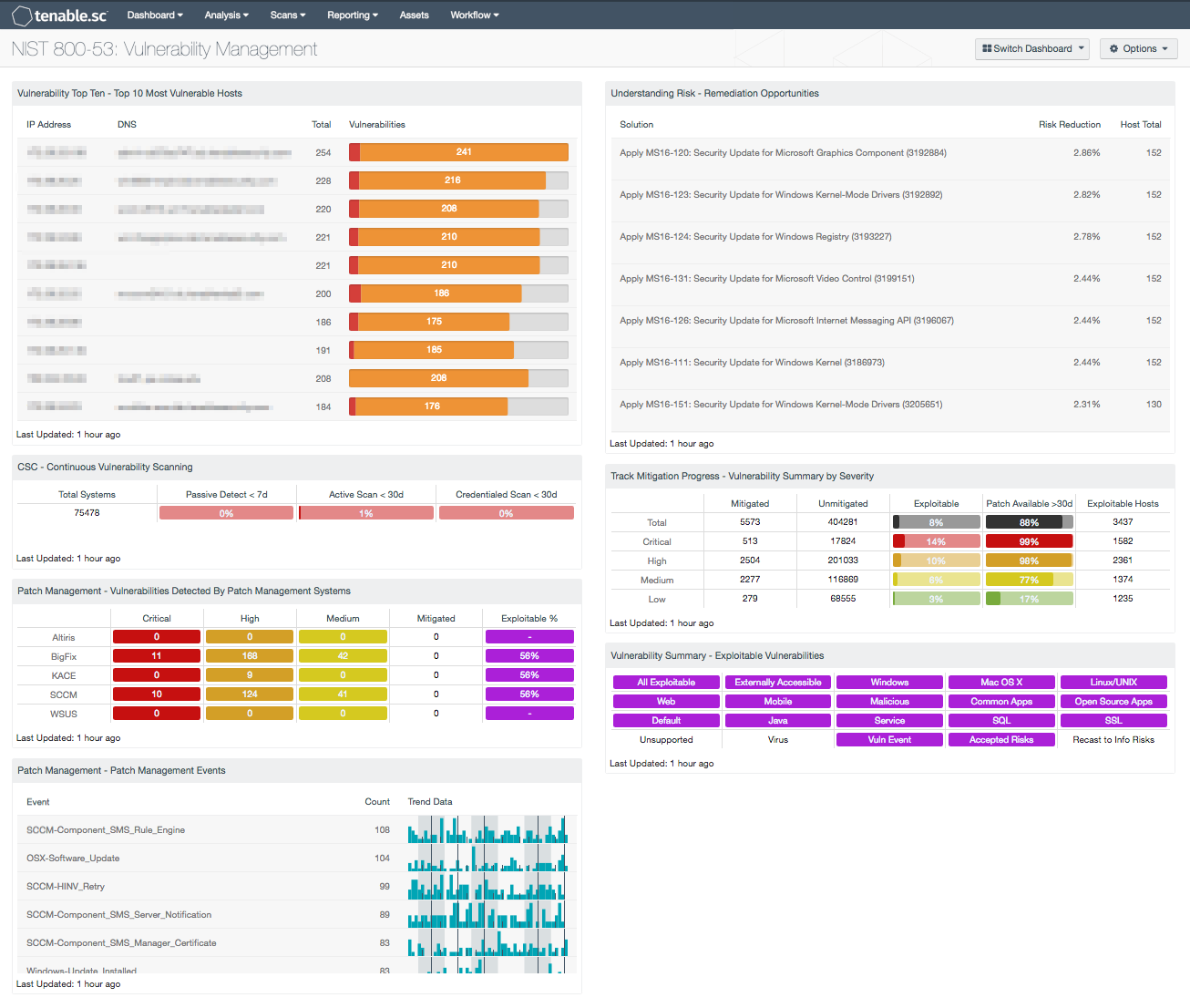
Vulnerability management plan template. The vulnerability management program utilizes. This is separate from your patch management policy instead this policy accounts for the entire process around managing vulnerabilities. Follow info techs methodology in assigning urgencies to vulnerabilities by examining the intrinsic qualities of the vulnerability as well as the sensitivity of the data and business criticality of the affected asset. O review change management reports for removal of affected software.
O verify that files or configuration changes remediated the vulnerability. Vulnerability management is the. Vulnerability scanning consists of using a computer program to identify vulnerabilities in networks computer infrastructure or appl ications. Vulnerability management procedure applies to the following controls found within the.
Documenting procedures for patch management is a vital part of ensuring cybersecurity. The next section of this paper examines t he project management aspects of plan do check act pdca as related to the vulnerability management program. Implement the vulnerability analysis and resolution capabilityoutlines an approach for putting. Scope of the program.
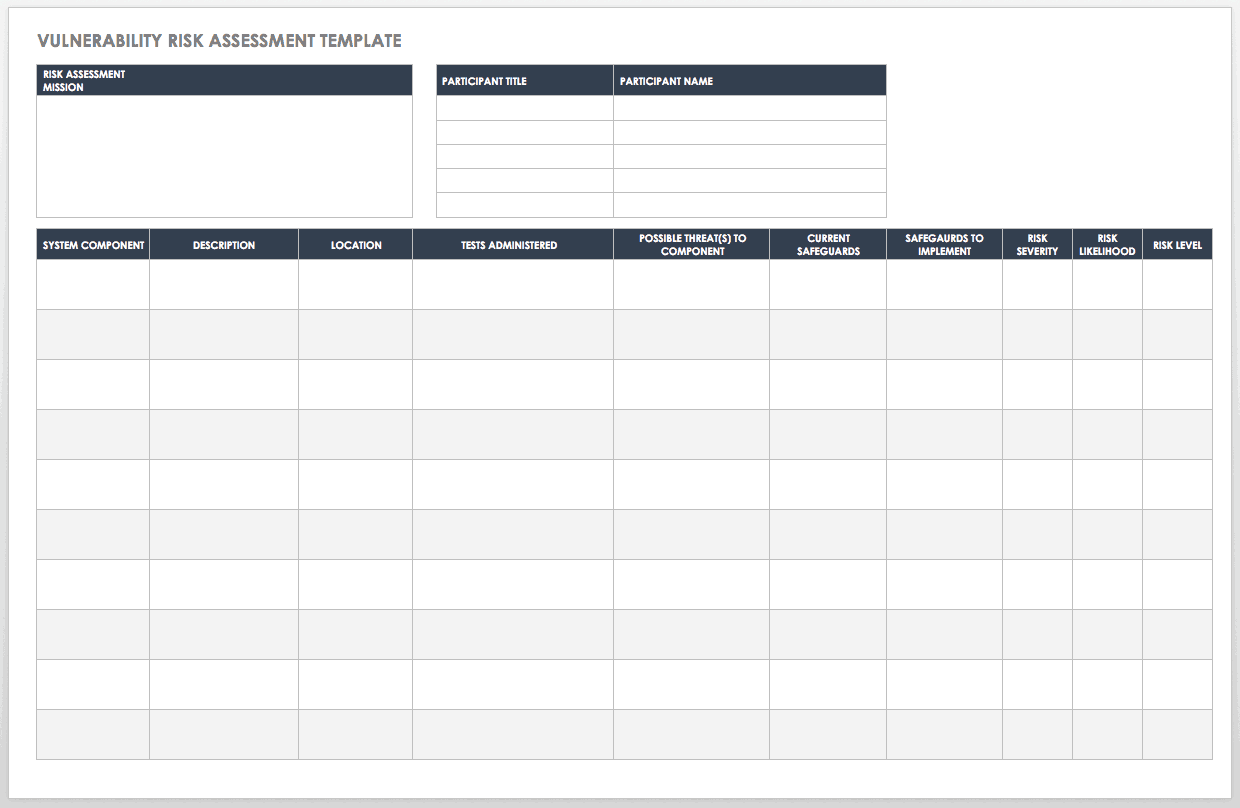
Vulnerability management vm is the means of detecting removing and controlling the inherent risk of vulnerabilities. Vulnerability assessments are not exploitative by nature compared to for example ethical hacking or penetration tests. Members of the vulnerability management team. This vulnerability management process template provides a basic outline for creating your own comprehensive plan.
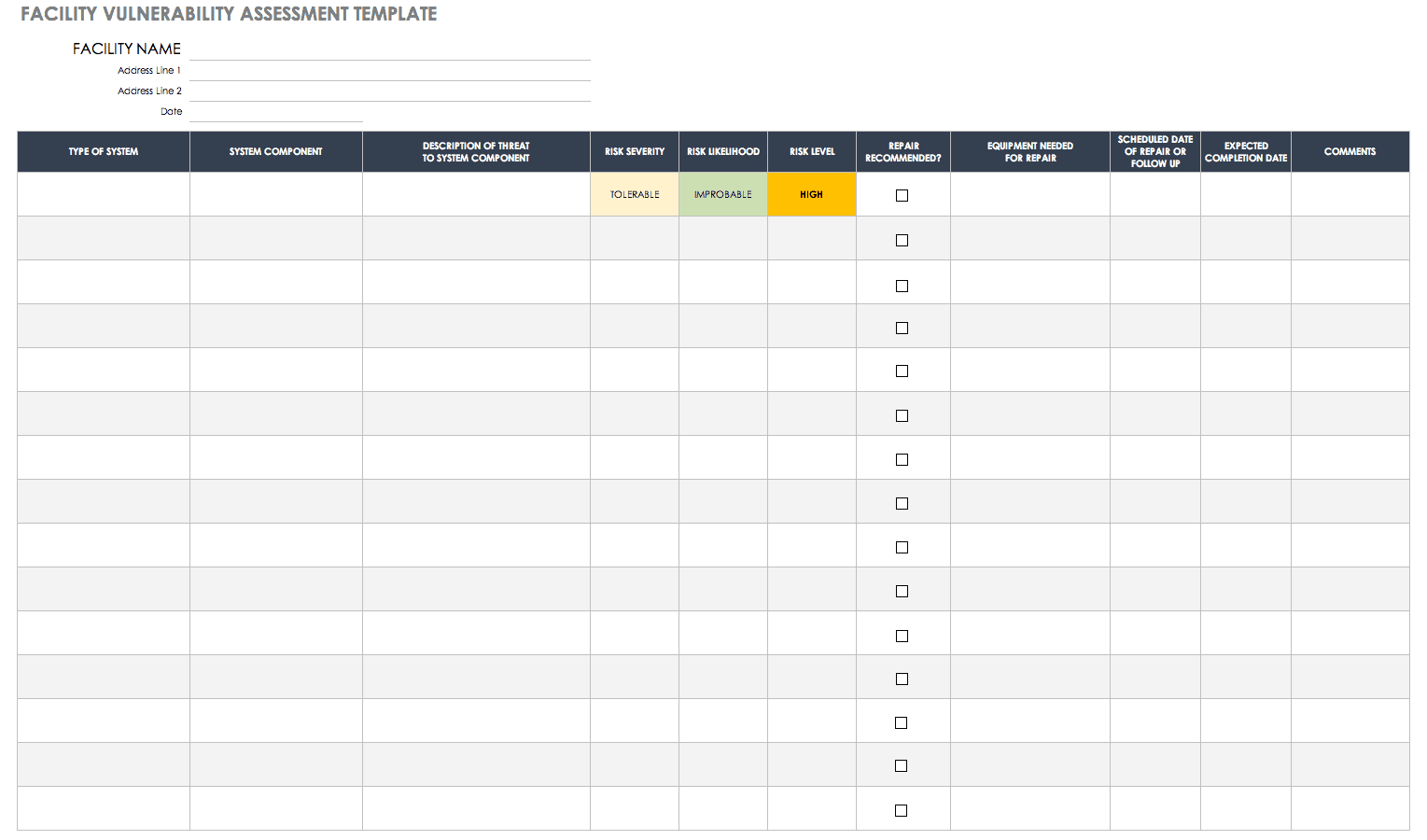
By creating a patch and vulnerability management plan organizations can help ensure that it systems are not compromised. The term vulnerability management is oft en confused with vulnerability scanning. Design and implement a vulnerability management program that identifies prioritizes and remediates vulnerabilities. This template will allow you to create a vulnerability management policy.
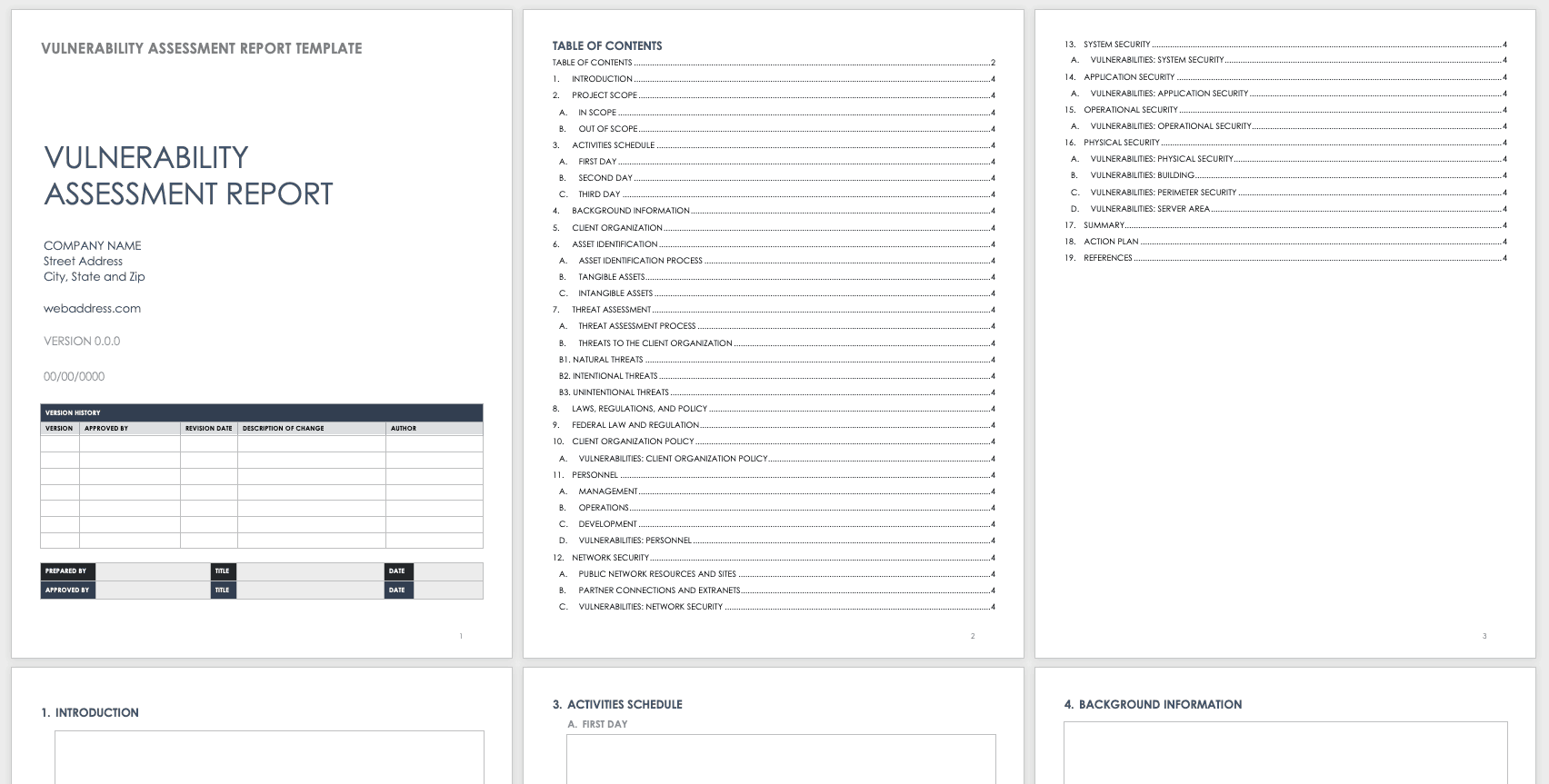
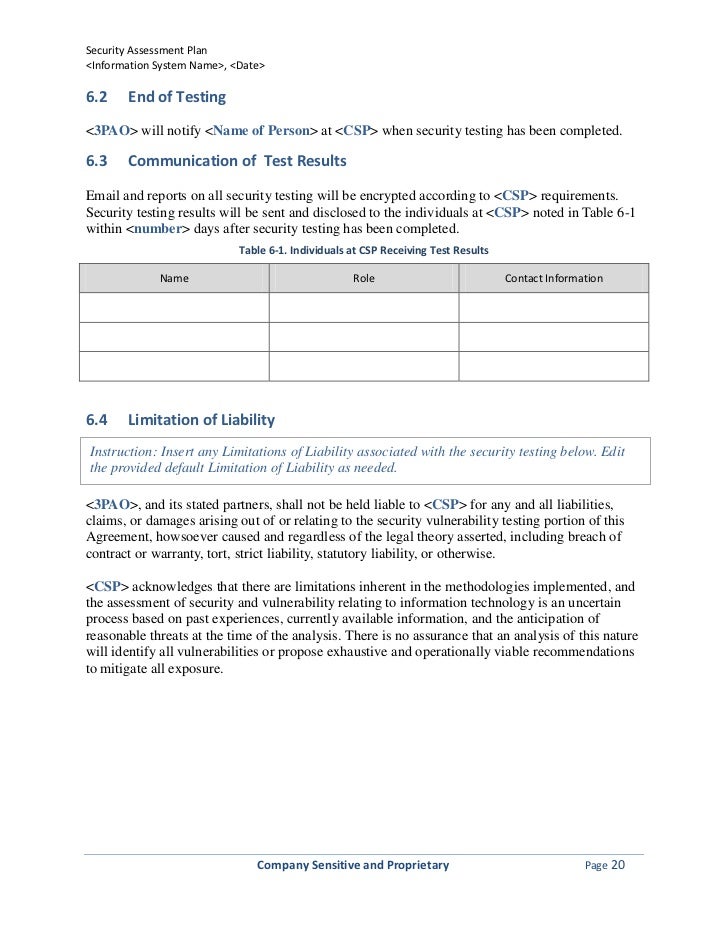
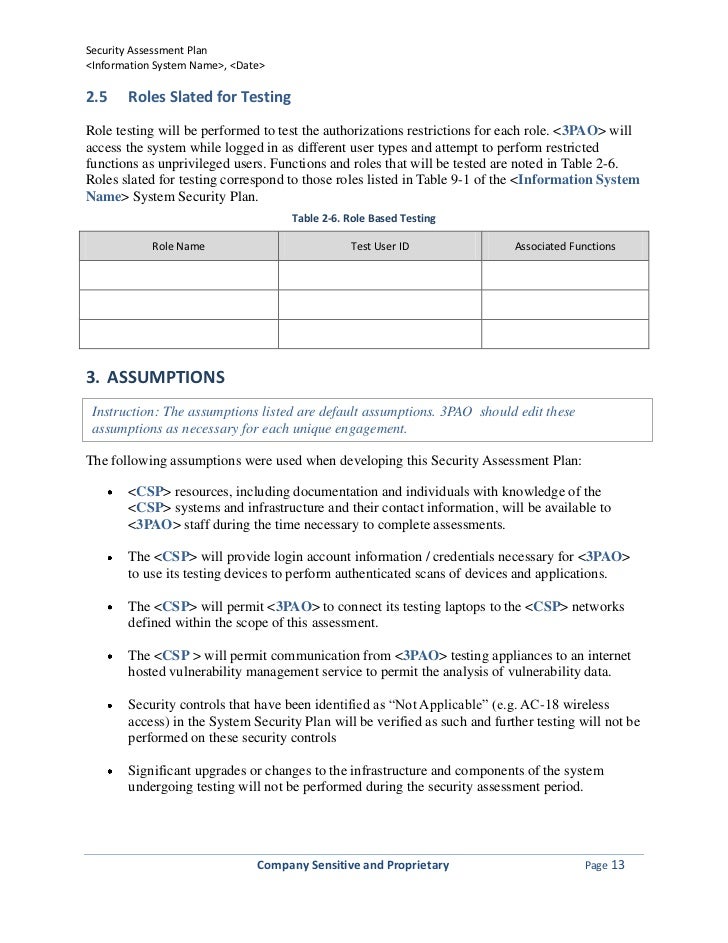
Despite the fact both are related there is an important difference between the two. The primary audience is security managers who are responsible for designing and implementing the program. A vulnerability management system or process can facilitate identification analysis and remediation of issues and thereby help enterprises realize the value of vulnerability assessment itself. This document provides guidance on creating a security patch and vulnerability management program and testing the effectiveness of that program.
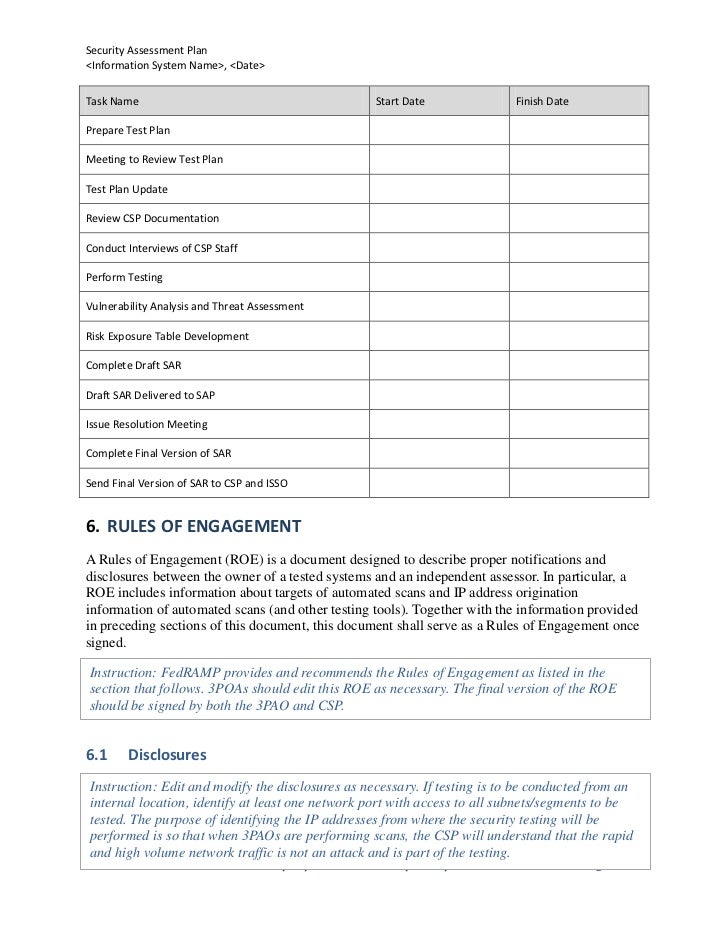
Configuration management plan risk assessment ra o ra 5 vulnerability scanning.