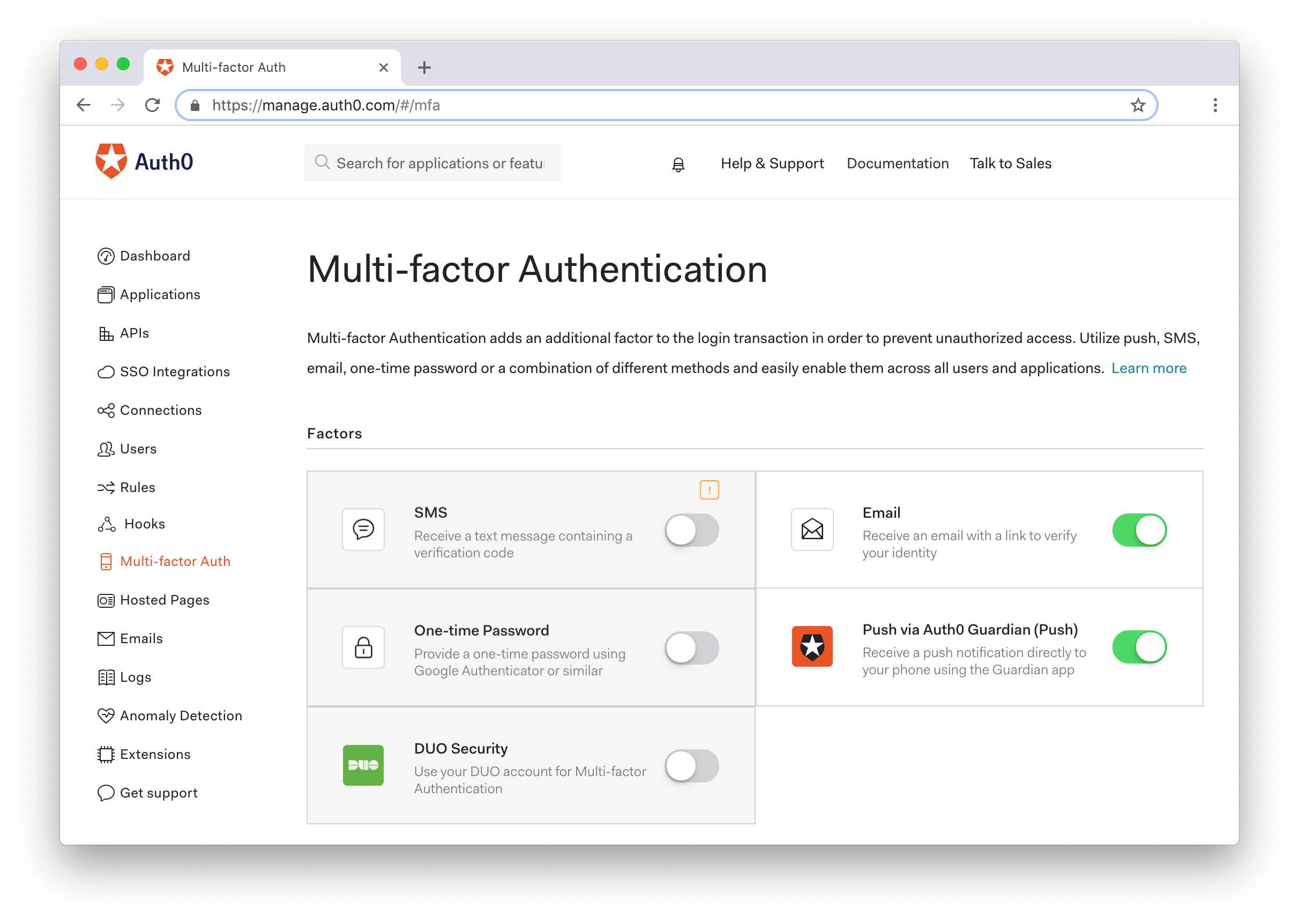
Mfa Policy Template

To enable a baseline policy.
Mfa policy template. The main highlights include. Enable a baseline policy. Set enable policy to on. Governing for results governance policies template introduction governance as defined here is the exercise of authority direction and c ontrol of an organization in order to ensure its purpose is achievedit refers to who is in charge of wha t.
Knowledge something they know possession something they have. Two factor authentication refers to using any two of these factors to authenticate a person before access to systems is granted. A non parameterized policy template is a policy template that does not have parameters. An administrator can assign this template to rps without any input needed and can make changes to a non parameterized policy template after it has been created.
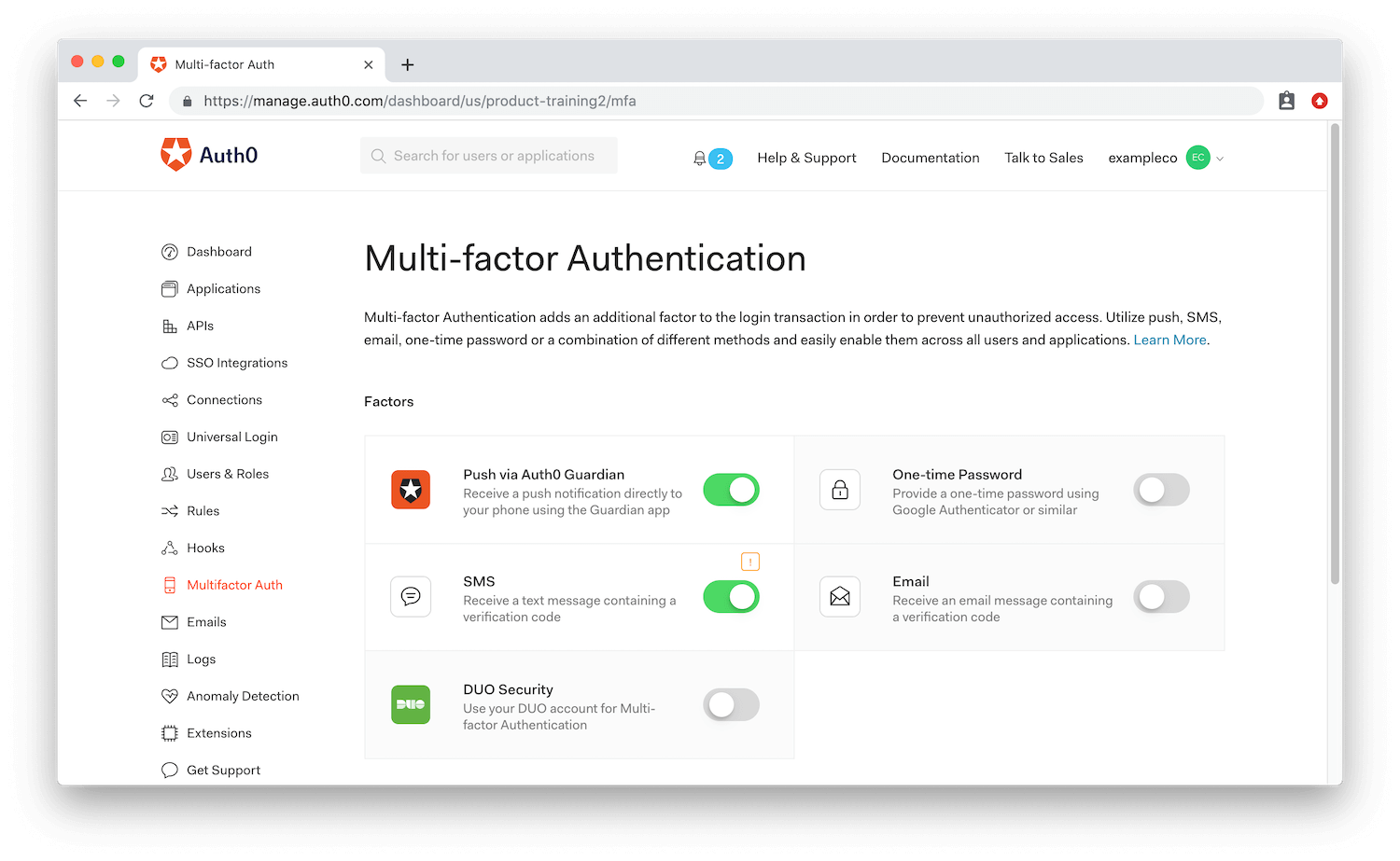
This template is based on our industry experience and incorporates our informed best practices as well as the latest guidance from nist. Rsa mfa agent for microsoft windows works with the rsa securid access cloud authentication service to require users to provide additional authentication to sign into windows computers whether they are online or offline. Multi factor authentication mfa is a method of computer access control in which a user is granted access only after successfully presenting multiple separate pieces of evidence to an authentication mechanism typically at least two of the following categories. Convenient authentication using approve.
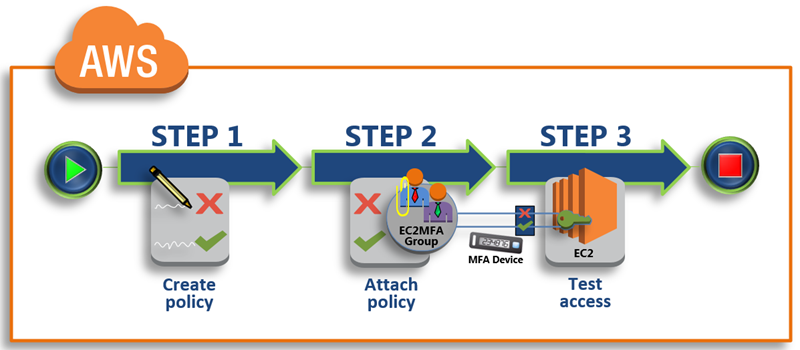
Browse to azure active directory conditional access. In the informationnetwork security realm policies are usually point specific covering a single area. In the list of policies select a baseline policy youd like to enable. The mfa policy ensures that more than one method of authentication is approved from more than one category of credentials when accessing data transaction or logging in on company assets.
Who sets the directi on and the parameters. The result is a short end user password policy for organizations to boost their access management and password security for 2018 and beyond. In the field of security there are three general factors that can be used to prove that you are who you claim to be. For example an acceptable use policy would cover the rules and regulations for appropriate use of the computing facilities.
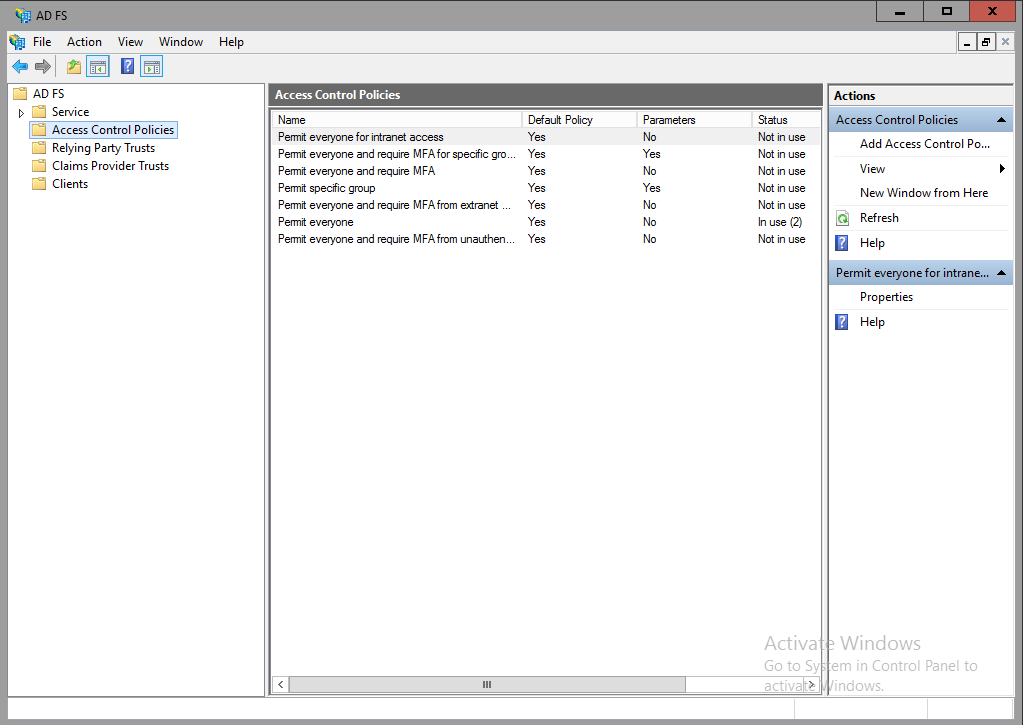
Multi factor authentication mfa requiring two or more authentication methods for a secure login. An example of this is the built in policy permit everyone and require mfa.